- Creating a pfSense Firewall
- Installing Kali Linux in Proxmox
- Configuring pfSense Firewall
- Configuring Suricata IDS in Proxmox
- Adding an Active Directory Forest to Proxmox
- Wazuh SIEM Setup in Proxmox
Windows Server Installation
In this guide, we’ll go through setting up an Active Directory forest in Proxmox. This guide will be broken up into several parts:
- Windows Server 2019 Installation – The server running Active Directory that acts as the domain controller
- Setting up DHCP and DNS services on the domain controller
- Adding users to the domain manually and through Powershell
- Windows 10 Enterprise Installation – Computers to connect to the domain
- Implement Group Policy Object (GPO) – Method that allows for creating settings for systems and groups of users
Active Directory Overview
At a high level, Active Directory centralizes the management of network resources and users in Windows environments. In an organization, you can have hundreds or thousands of users, computers, and devices such as printers and networking equipment that need to be managed. Being able to manage all of these resources from one interface is what makes their management possible at a large scale.
Some of the more important aspects of managing these resources includes maintaining the authentication and authorization policies for users and computers and keeping the software on computers up to date. Using the management of users as an example, by default, users shouldn’t be able to access every network resource or even every feature on a computer. That access should be based on the role of the user. Rather than assigning privileges on an individual basis, with Active Directory, you can create pre-configured categories of roles of varying privileges and then place users in the appropriate category.
Windows Server Installation
Download Windows Server 2019 Iso
Download the evaluation copy: https://info.microsoft.com/ww-landing-windows-server-2019.html
You can use dummy information on the form.
Download the 64-bit version and upload it to Proxmox.
We also need the VirtIO drivers. The direct download for the latest stable version is here:
https://fedorapeople.org/groups/virt/virtio-win/direct-downloads/stable-virtio/virtio-win.iso
The links for the iso can also be found in the Proxmox docs:
https://pve.proxmox.com/wiki/Windows_VirtIO_Drivers#Wizard_Installation
Create VM
Create a new VM.
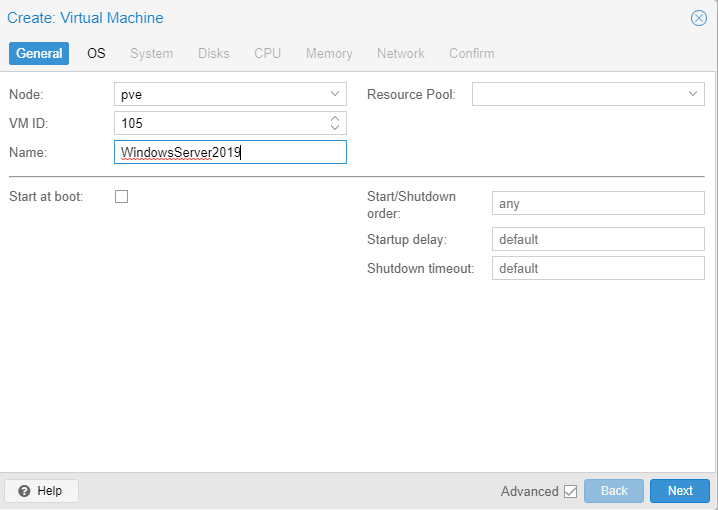
Choose the Windows Server 2019 iso. Select Microsoft Windows as the OS.
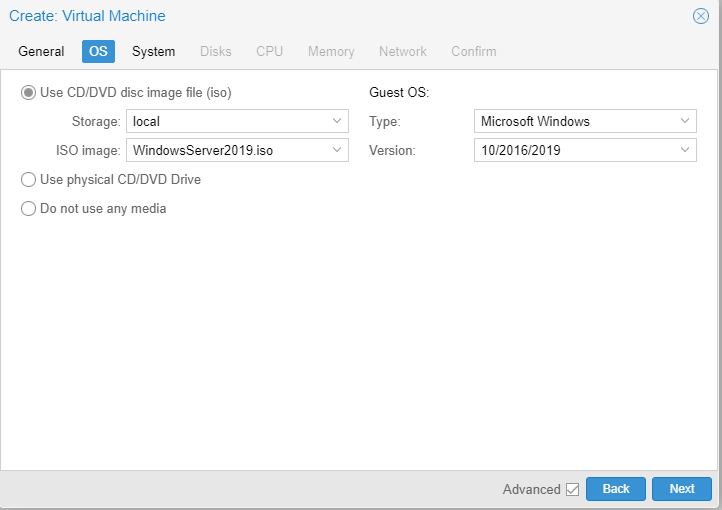
Check the Qemu Agent box. If you don’t see the option, make sure the advanced box is checked on the bottom of the window.
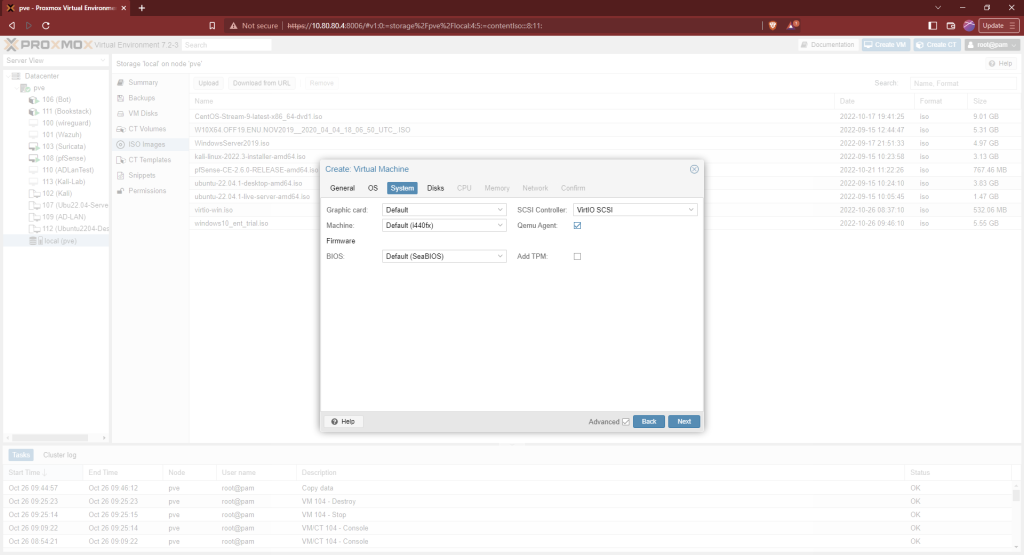
Choose “SCSI” as the bus device. Select “Write Back” for cache and check the “Discard” box.
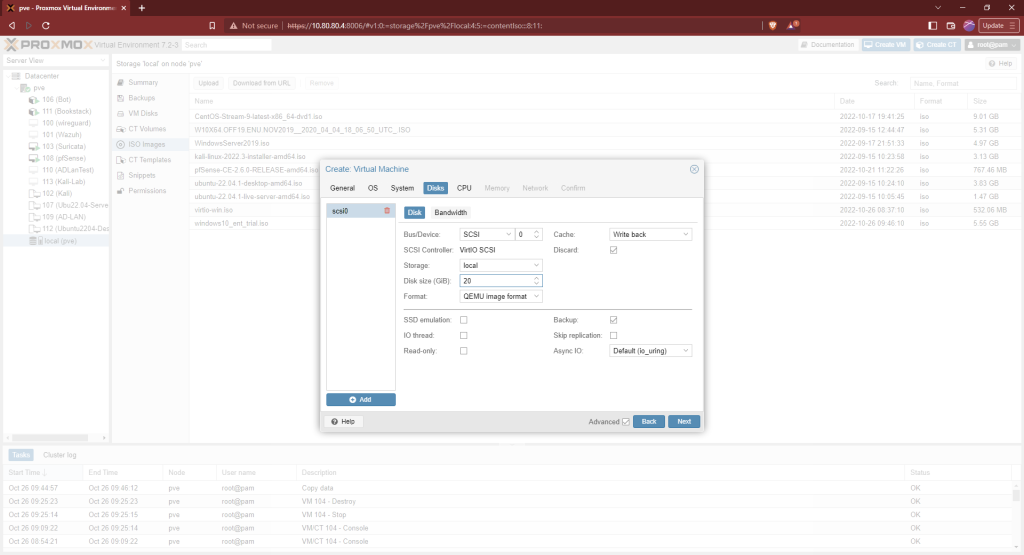
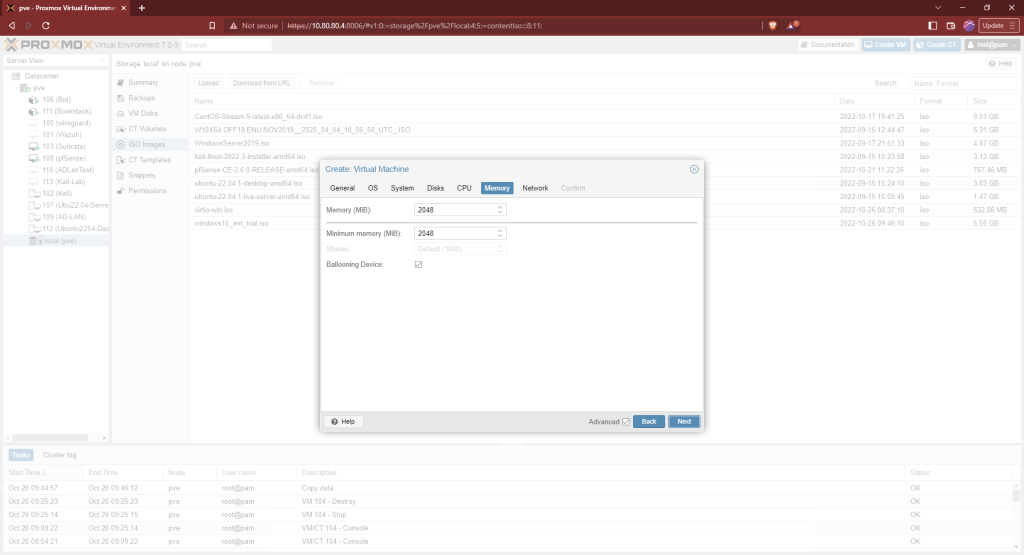
Select the number of cores appropriate for you host system’s resources. I’m using 2 since Proxmox server is being hosted on an older laptop. I’m also going with 2GB of RAM.
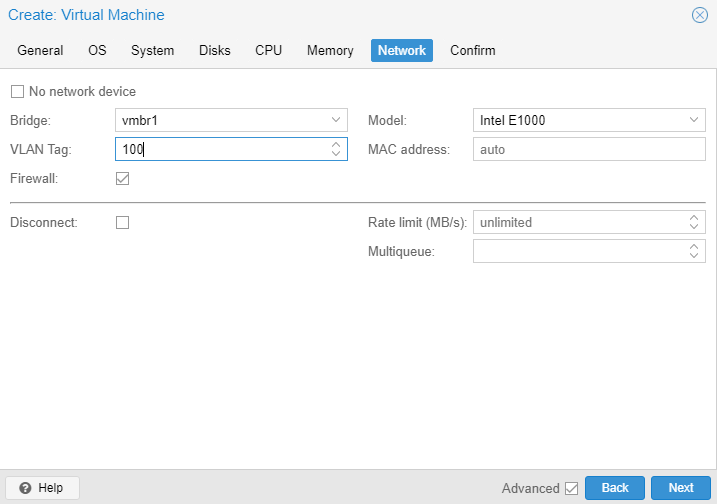
This machine is going to be our domain controller so the network interface will be vmbr1. The VLAN tag is 100. Since this is a learning environment, this domain controller will be on on the same subnet as the other machines connected to it. In a production environment, the domain controller or controllers will be on a separate subnet.
Change the “Model” to “VirtIO (paravirtualized). Then finish making the VM. Don’t start it yet.
Click on the WindowsServer2019 node that was just made. Click on “Hardware” and then add a new CD/DVD drive.
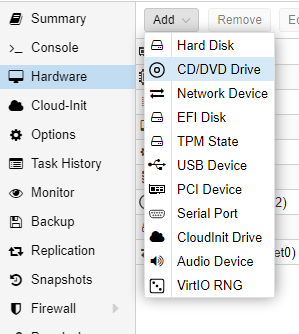
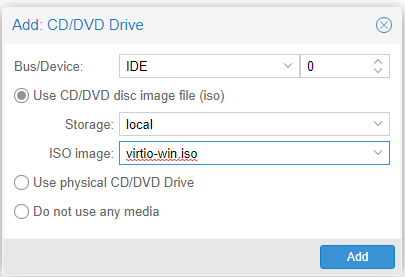
Choose the virtio iso that was downloaded earlier. Now, start the machine.
Installation
Choose next at the first screen then choose install.
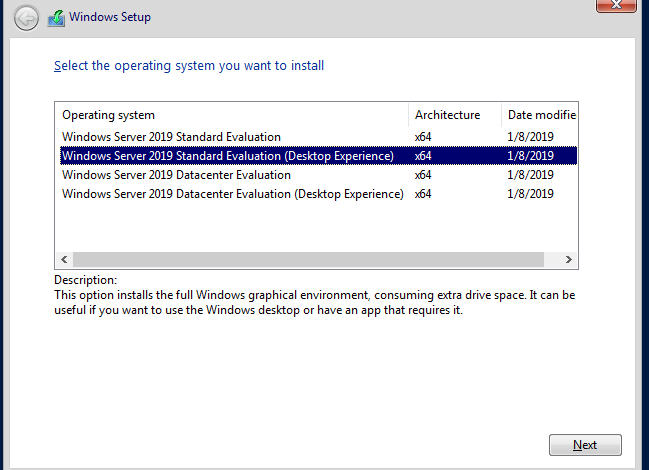
Choose the Desktop Experience of Windows Server 2019. Accept the license terms.

Choose “Custom Install.”
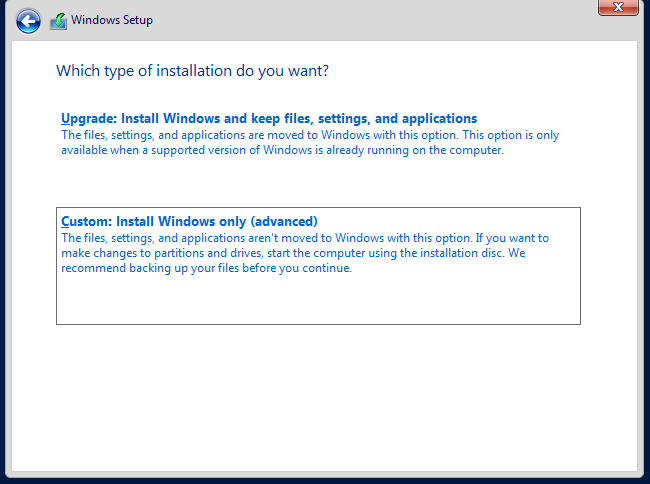
At the next screen, you won’t see a hard drive to choose. That’s normal. Click “Load Driver” from the options at the bottom.
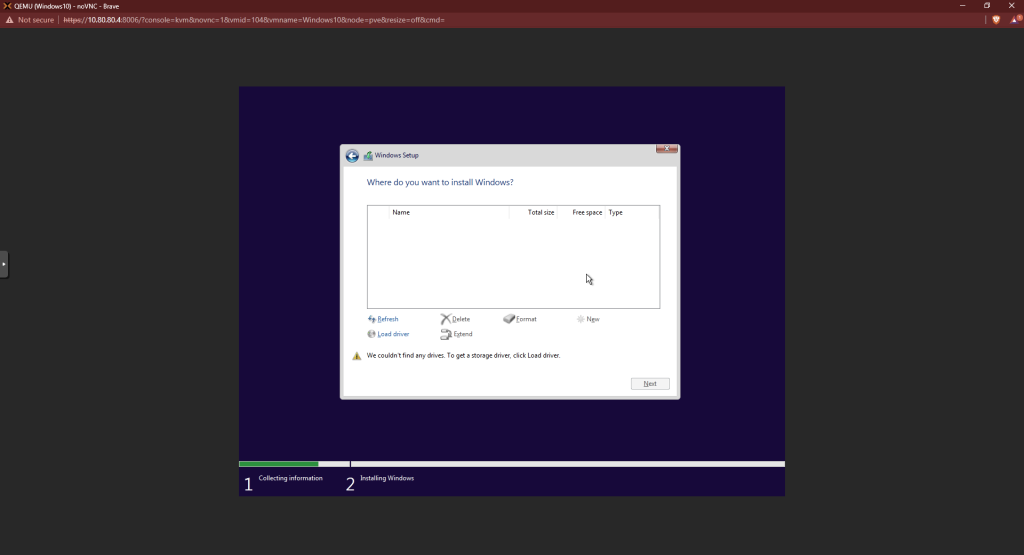
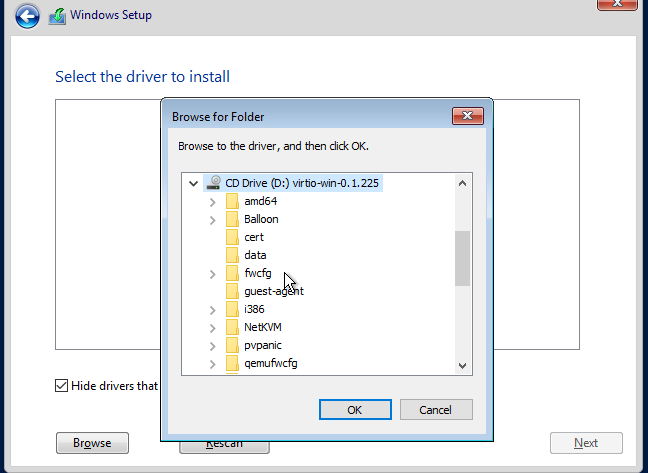
Choose browse at the next screen. Open the drive with the virtio disc. Expand the “vioscsi ” folder, then the “2k19” folder. Click the “amd64” file then hit OK.
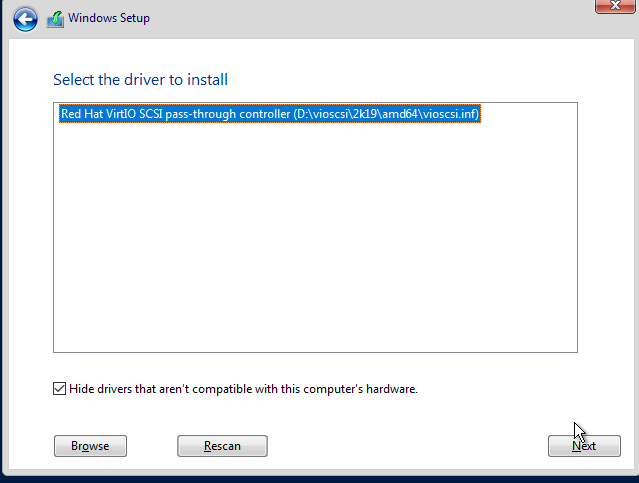
A driver should now show up on the screen. Hit ‘next.”

Back at the main screen, you should see there’s a hard drive now. Before continuing, we need to install the network drivers. Click “Load Driver” again.
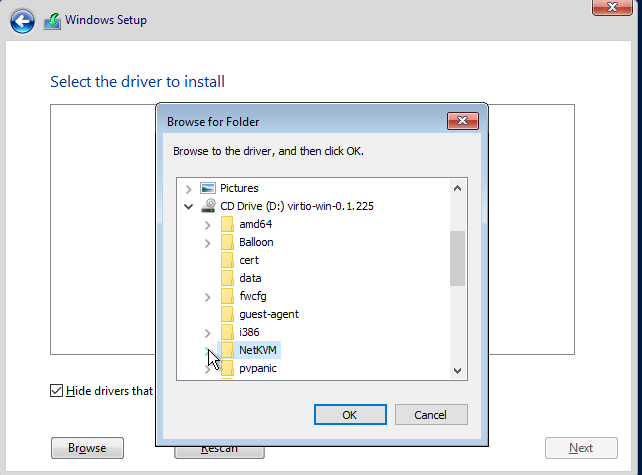
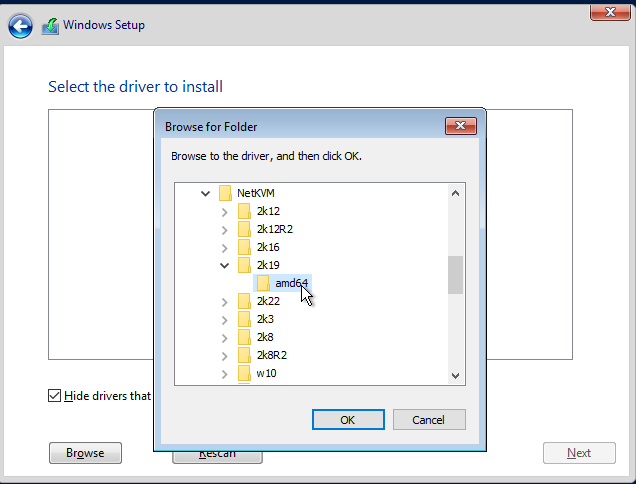
Choose the driver, then hit “Next.”
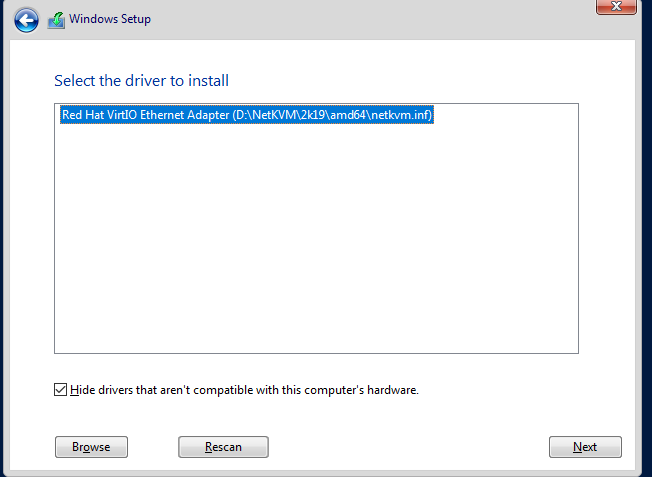
Back at the initial screen, click next. Wait for the installation to finish.
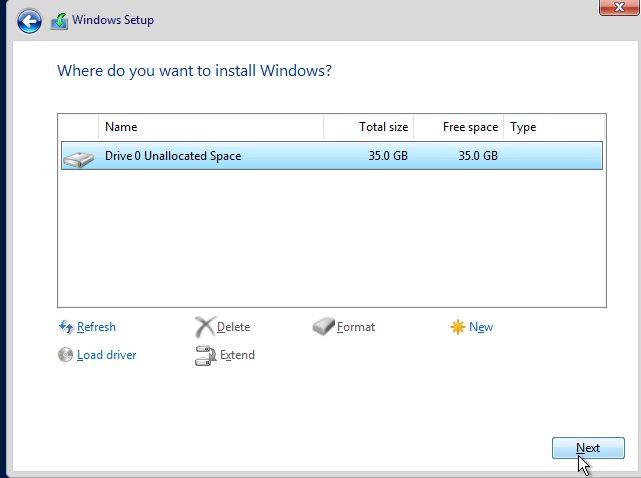
Make an admin password.
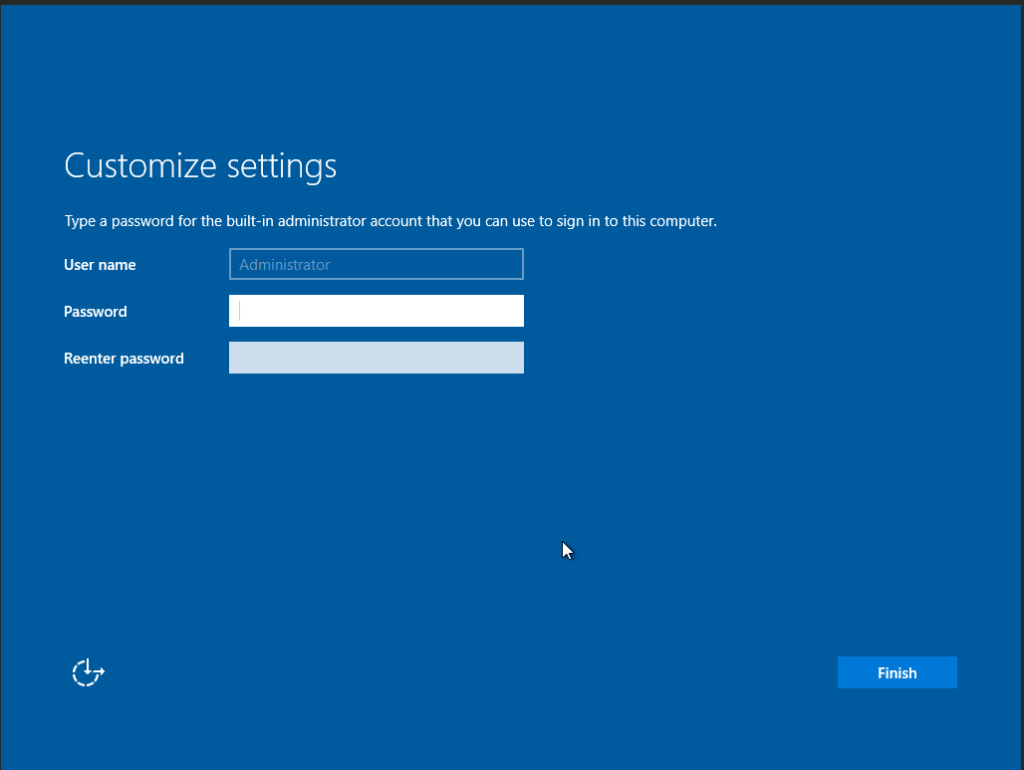
You should now be at the login screen. On Proxmox, to hit ctrl + alt +delete, click the menu arrow on the left side of the screen. This brings up a menu. Press the first button on the top, then the bottom button of the next menu that comes up.

Log in with the password you created.
Active Directory Configuration
Configure Network Settings
Since DHCP isn’t configured on this interface, we need to manually configure the network settings.
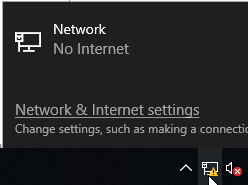
Click the network icon on the bottom right of the screen. Then click “Network & Internet Settings.”
Click “Change adapter options.”
Click “Ethernet Instance 0.”
Click “Properties”, then “Internet Protocol Version 4 (TCP/IP).”
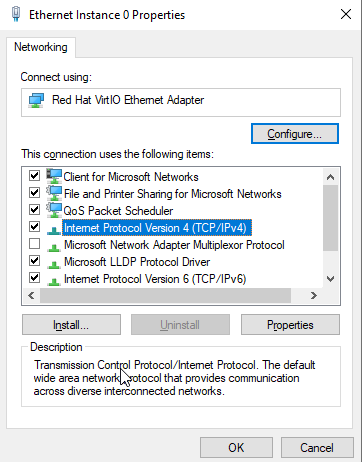
This machine is on the 10.0.20.1/28 network. We’ll give it an IP address of 10.0.20.2, the subnet mask is 255.255.255.240, and the default gateway is 10.0.20.1. Since this server is serve as the DNS server for this network as well, the preferred DNS will reference the machine itself.
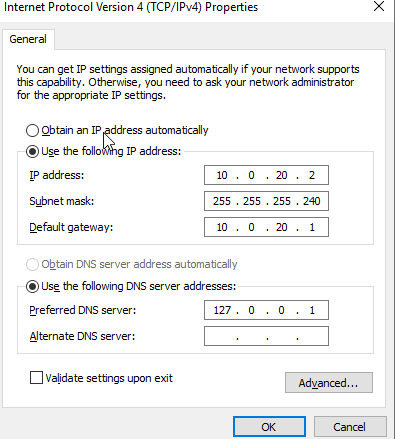
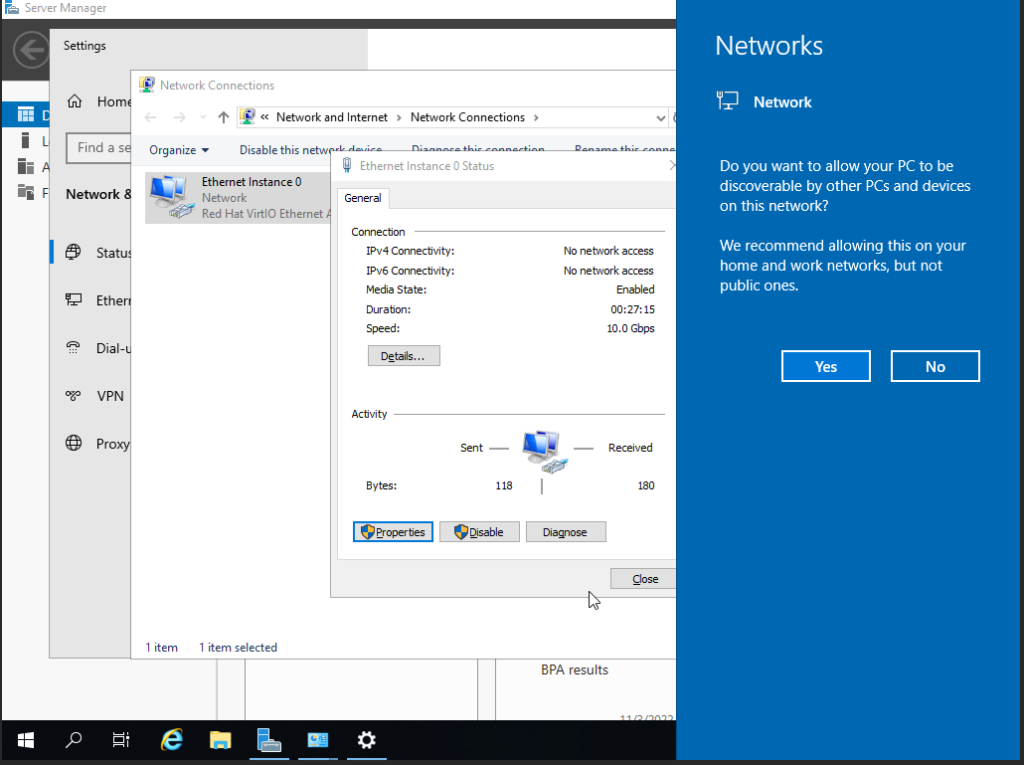
Press OK and to exit the menus and a prompt to connect to the network should show up. Choose “yes.”
Rename the Server
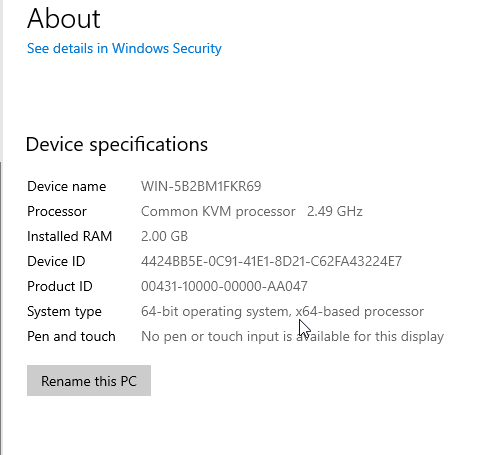
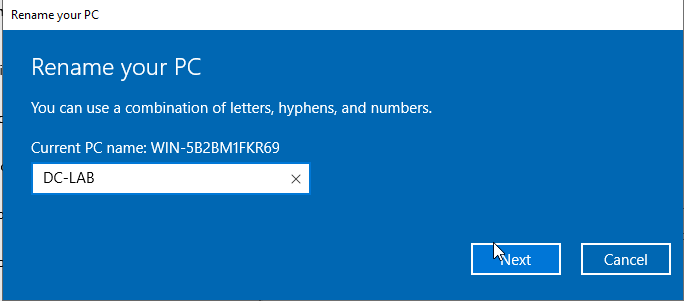
Click the start button, then click “settings.” In the search bar, type “About PC.”
Click Rename this PC and choose a new name for this machine. Restart the machine when prompted.
Install Domain Controller Services
Before continuing, take a snapshot of the machine.
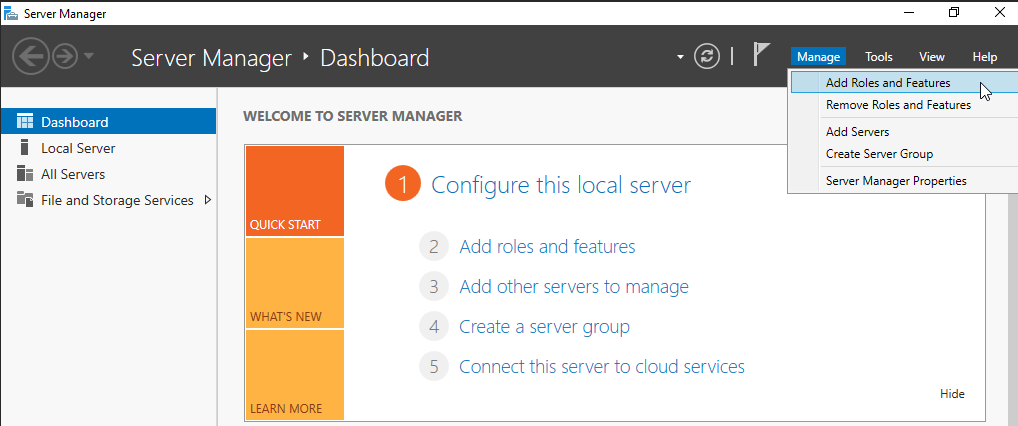
When the machine restarts, in the server manager, choose “Manage,” then “Add Roles and Features.”
Choose “Next” at the first screen.
Select “Role-based Installation” the next.

No changes needed on this screen.
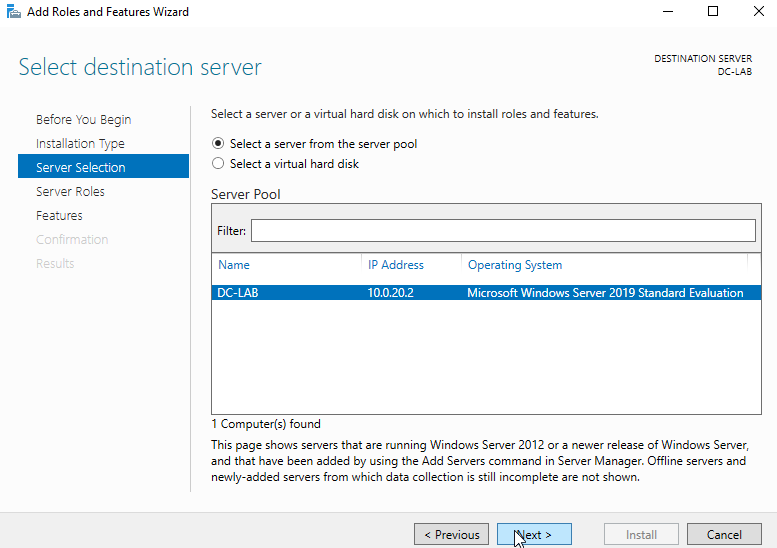
Add “Active Directory Domain Services” and “DNS Server.” Click “Add Features” when prompted after clicking the boxes. Then click “next.”
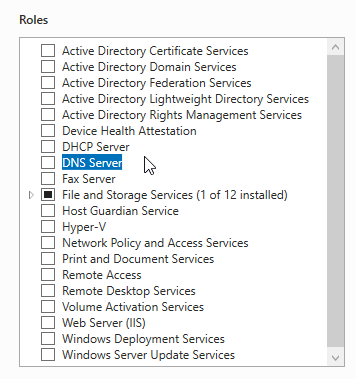
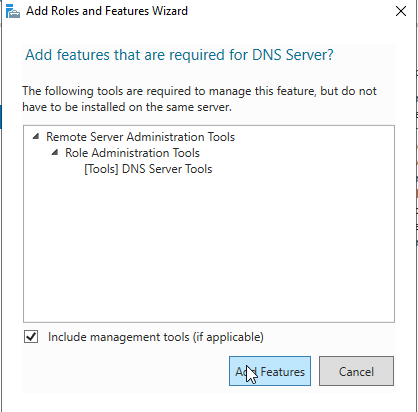
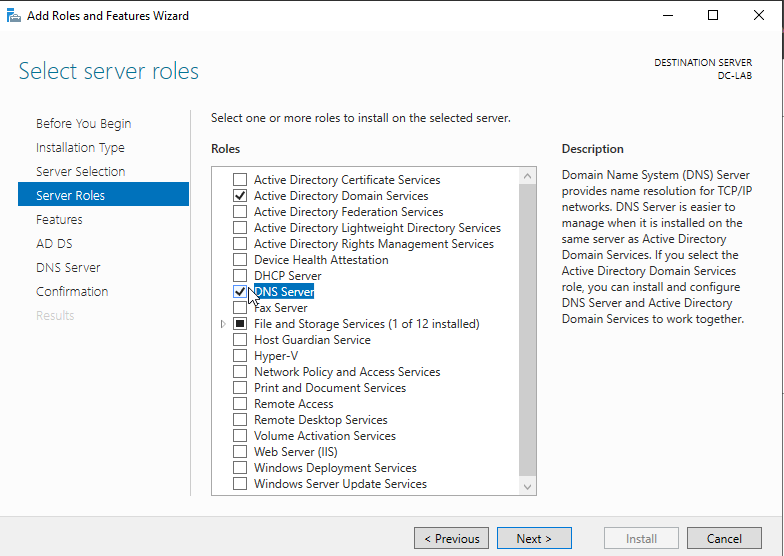
Continue hitting next until you get the confirmation screen that lets you click “Install.” Click “Install.”
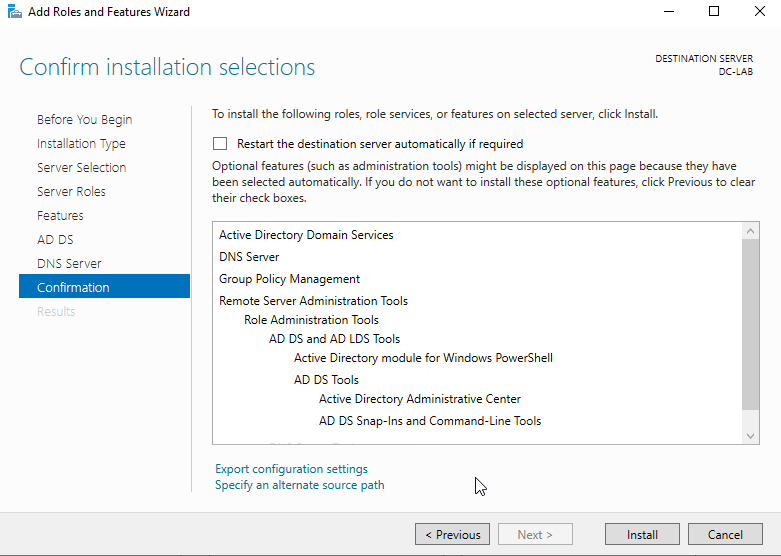
On the server manager, there should be a notification. Click on it and click “Promote this server to a domain controller.”
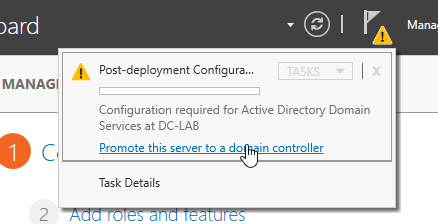
Choose “Add a new forest” and select a name for the root domain name. Select “Next.”
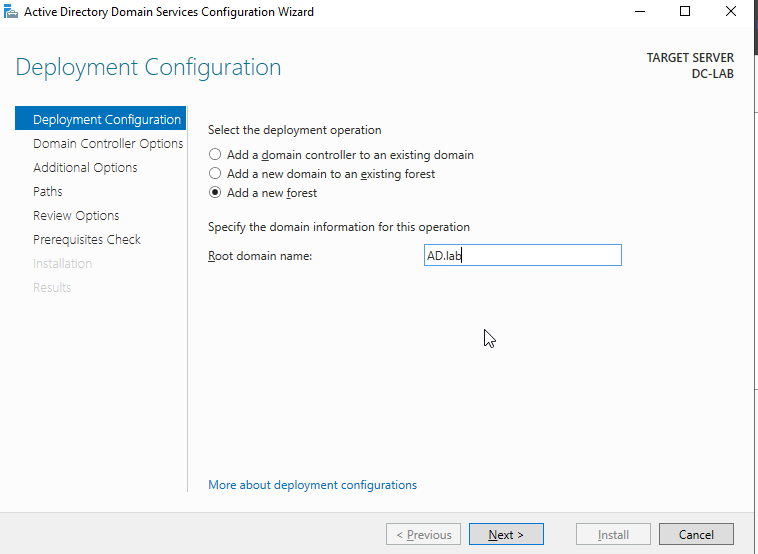
Leave the settings as is and make another password. Click “next.”
Leave this box unchecked and click “next.”
Wait for the NetBIOS name to fill in, then click “next.”
No changes are needed. Click “next” until you’re at the prerequisites check. Then “install.” Wait for the machine to restart then log back in.

Domain Controller DNS Services
The next step is to set our pfSense gateway as the downstream DNS resolver to handle any DNS queries the domain controller cannot resolve.
In the search bar, type in ‘DNS” and open the DNS app.
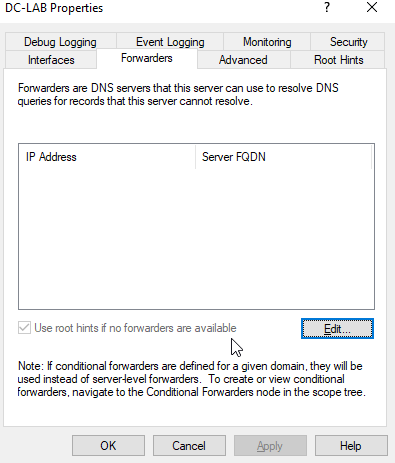
Click on the node of your domain, then double-click forwarders.

Click “edit,” then enter the IP of the default gatway.
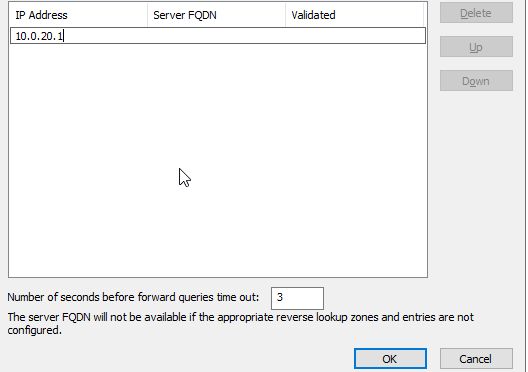
Configure DHCP Server
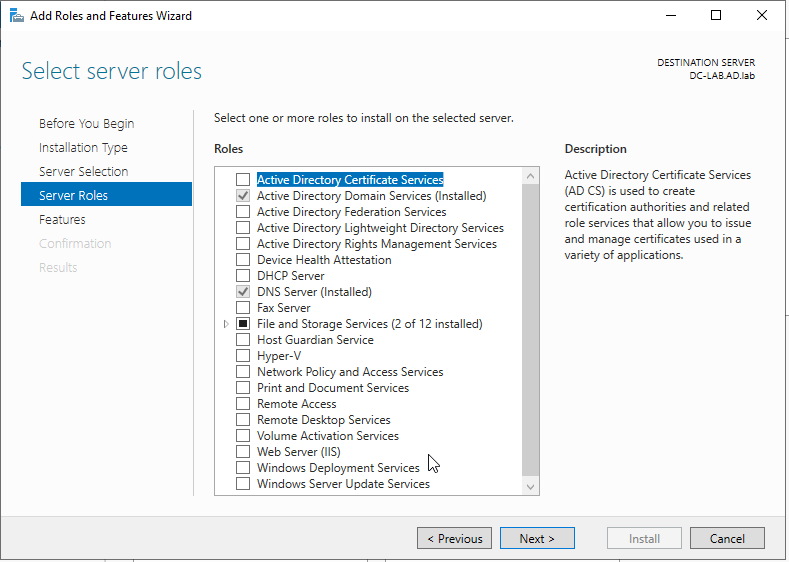
Back in the server manager, click on “Add Roles and Features.”
Click “next” until you get to the screen to add features.
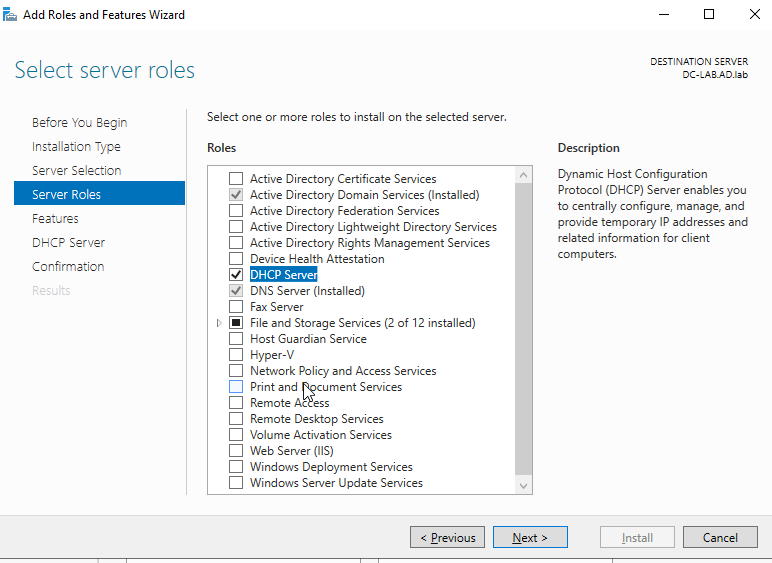
Click the box for “DHCP Server.” Click “Add Features” when the next screen pops up. Then click “next.”
Keep clicking “next” until you can click “install.” Then install.
After it’s done installing, click “Complete DHCP Configuration.”
Click “next” at the first screen, then “commit.” Close the windows.
Click on your domain controller node, right-click on “IPv4” in the middle window, then choose “New Scope.”
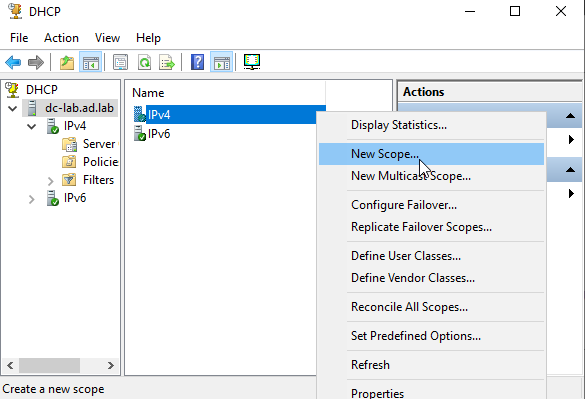
Click “next.” Add a description for the DHCP scope.
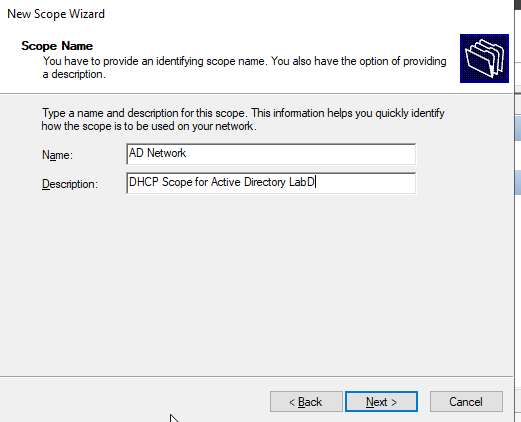

Enter the IP address range of your network, starting at the 3rd IP address of the range since the default gateway and this domain controller are using the first two IPs already.
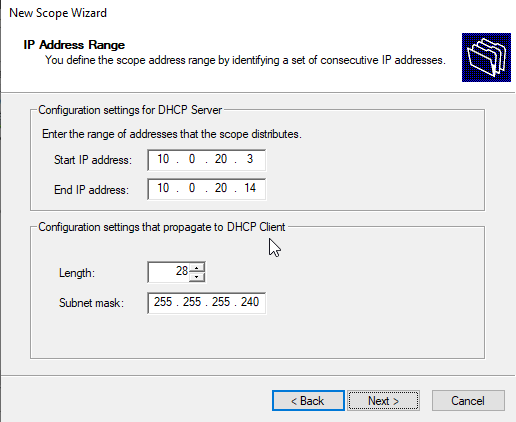
No exclusions will be set for now. Click “next.”
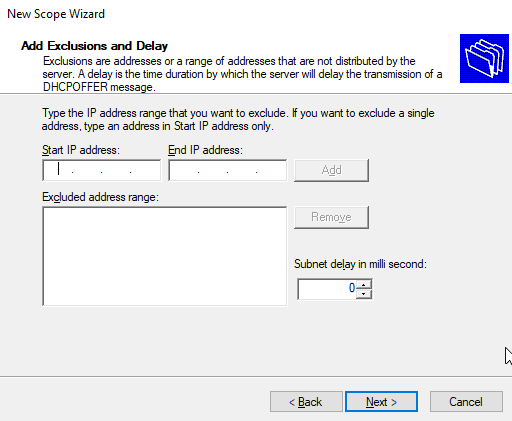
Set the client leases for one year, the click “next.”
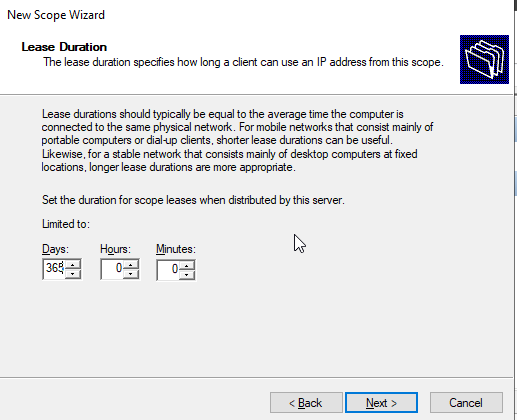
Configure the options now.
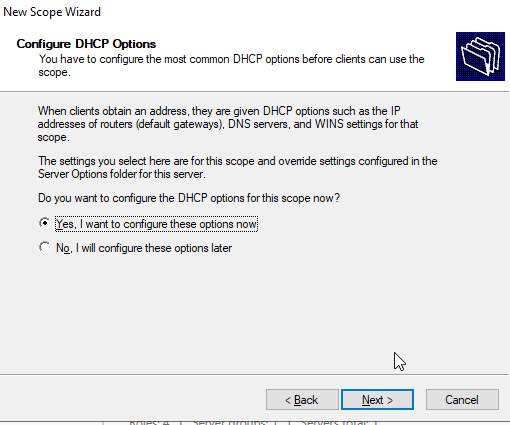
Enter the default gateway. Make sure you click “Add” and it shows up in the box.
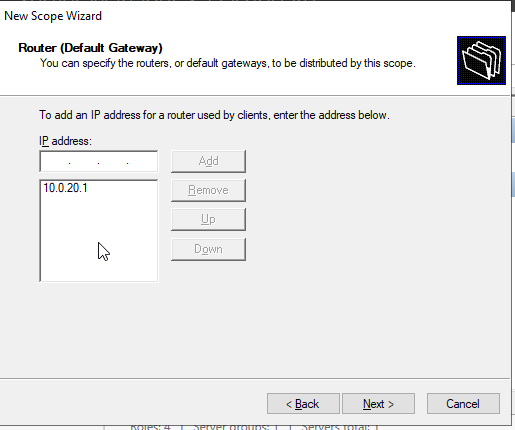
The parent domain name and IP address should be correct. Hit “next.”
There won’t be a WINS server on this network so just click “next.”
Make sure the option to activate the scope now is selected, then hit “next.” Then “finish.”
Adding Users and Computers to Domain
Add Users to Domain Manually
First, we’ll go through adding users the manual way as a demonstration. Back in the server manager, click “Tools” then “Active Directory Users and Computers.”
Right-click on your domain and choose “New” then “User.”
Add in the user information. Then hit “Next.” Then enter the password and options.
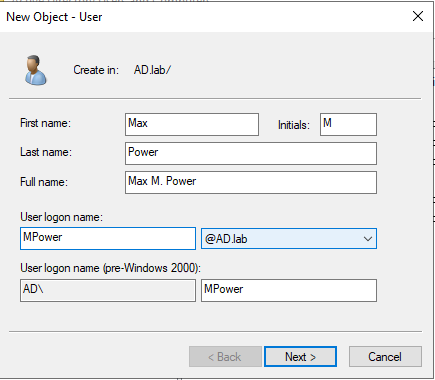
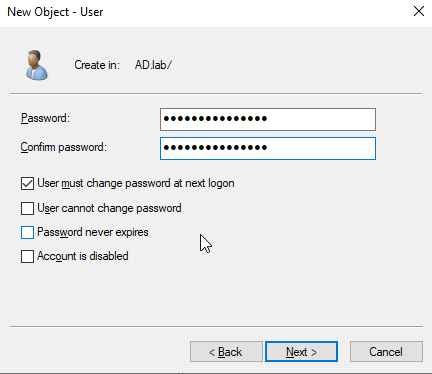
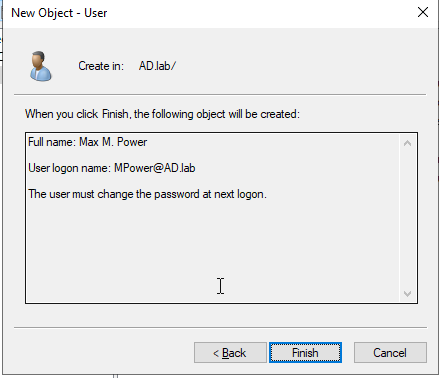
Our new user now appears in our list. We’ll leave the new user here for now since we’re about to create more.
Adding Users with Powershell
Download the Script
With Powershell, we can add several users at once instead of one at a time like we just did.
The script can be found here: https://github.com/joshmadakor1/AD_PS/archive/master.zip (Credit to Josh Madakor for making the script)
To get the script onto the VM, you can either use Remote Desktop Protocol if on a Windows machine or download it from the VM itself. To use Remote Desktop, make sure your firewall rules are open for port 3389. You may also need to add a static route in your router to allow traffic to the gateway of the Active Directory network.
If downloading from the VM itself, make sure to turn off “IE Enhanced Security Configuration” from the local server options temporarily.
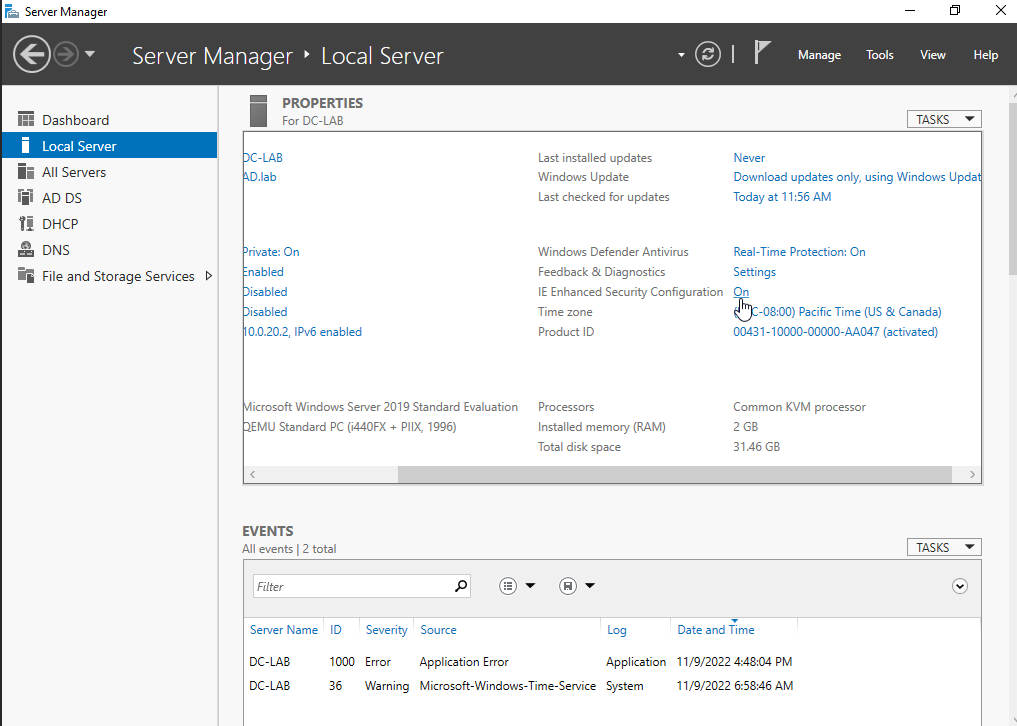
Then, go to the following link inside the VM: https://github.com/joshmadakor1/AD_PS/archive/master. Download the file to your downloads folder.
Unzip the file.
Script Explanation
Open the text files to see it’s a list of names. These are the users the script will add our domain.
Right click on the “1_CREATE_USERS” to view the script.
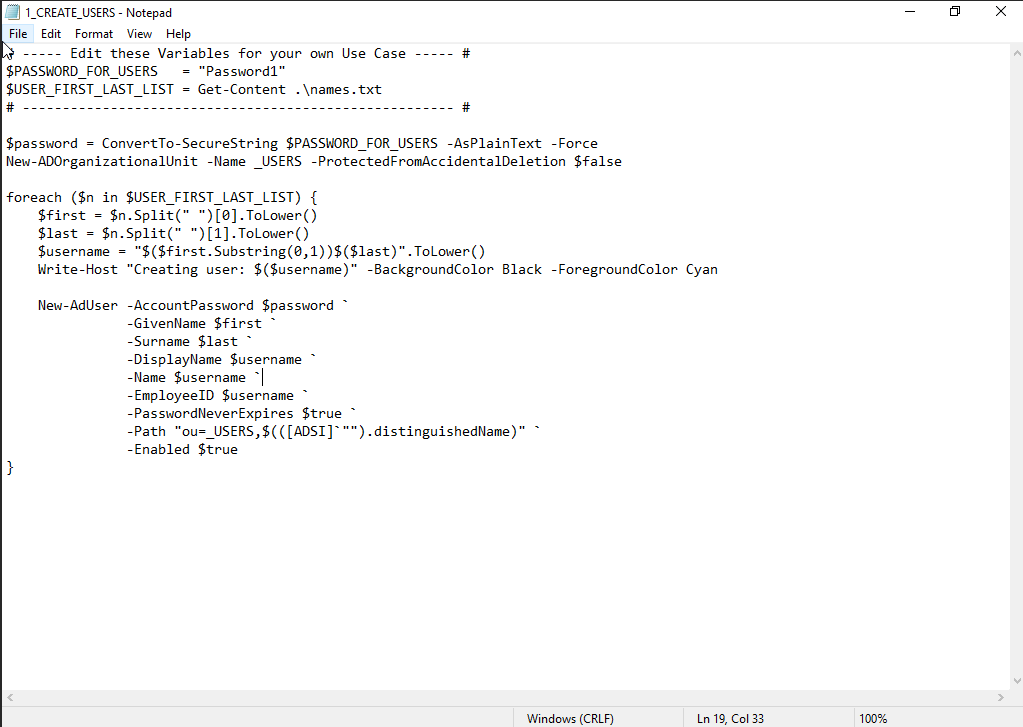
Let’s go through what this script is doing:
The first section creates two variables. The first one is for the default user password. The second stores all of the names in the text file to $USER_FIRST_LAST_LIST.
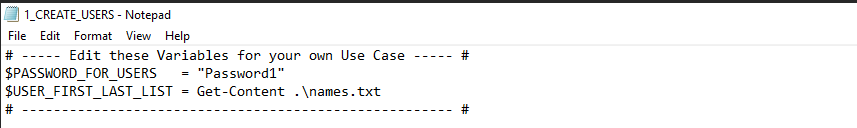
The next section converts the password variable to a encrypted credential object and creates an OU (organization unit) called _USERS.
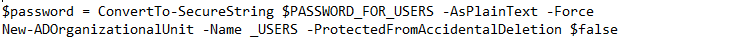
This section creates a loop that goes through the name list and combines the first initial of each name with the full last name. For example, Suzanne Nell becomes snell.
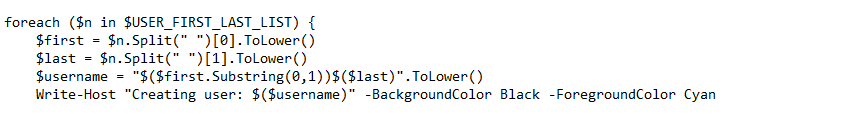
The final section is automating the attributes of the users.
Running the Script
Right click “1_CREATE_USERS” and click “Run with Powershell.”
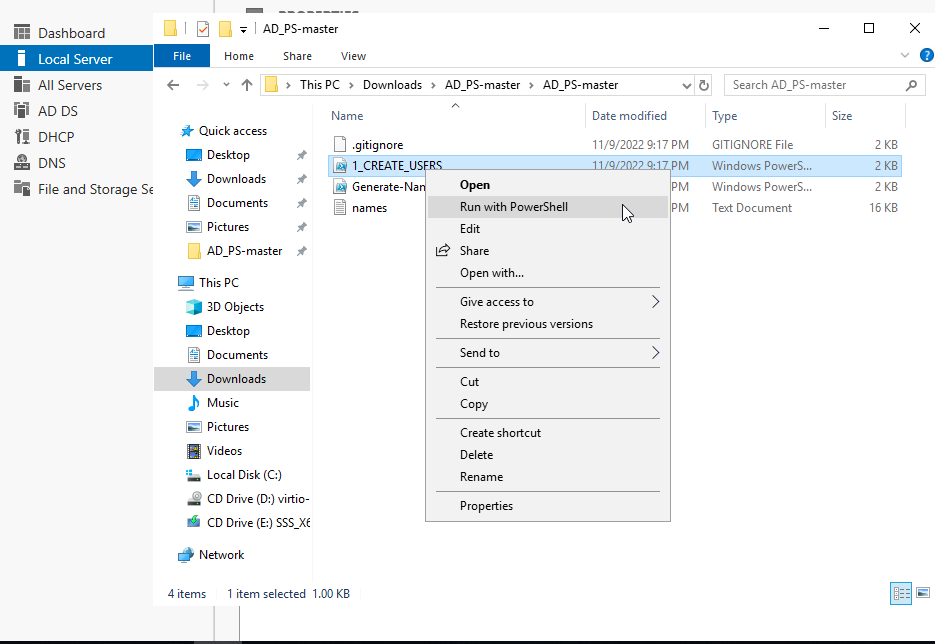
The script will start running and add users. You can press ctrl + c to stop the script early.
Go back to the Server Manager. Check the Active Directory Users and Computers and you should see a new OU with the new users in it.
Add Computers to Domain
Windows 10 VM Setup
Installing the Windows VM will be similar to the Windows Server install.
Go to this page to download a trial version of Windows 10 Enterprise. You can use dummy information.
https://info.microsoft.com/ww-landing-windows-10-enterprise.html
Download the 64-bit version and upload it to Proxmox.
We also need the VirtIO drivers. The direct download for the latest stable version is here:
https://fedorapeople.org/groups/virt/virtio-win/direct-downloads/stable-virtio/virtio-win.iso
The links for the iso can also be found in the Proxmox docs:
https://pve.proxmox.com/wiki/Windows_VirtIO_Drivers#Wizard_Installation
Create a new VM.
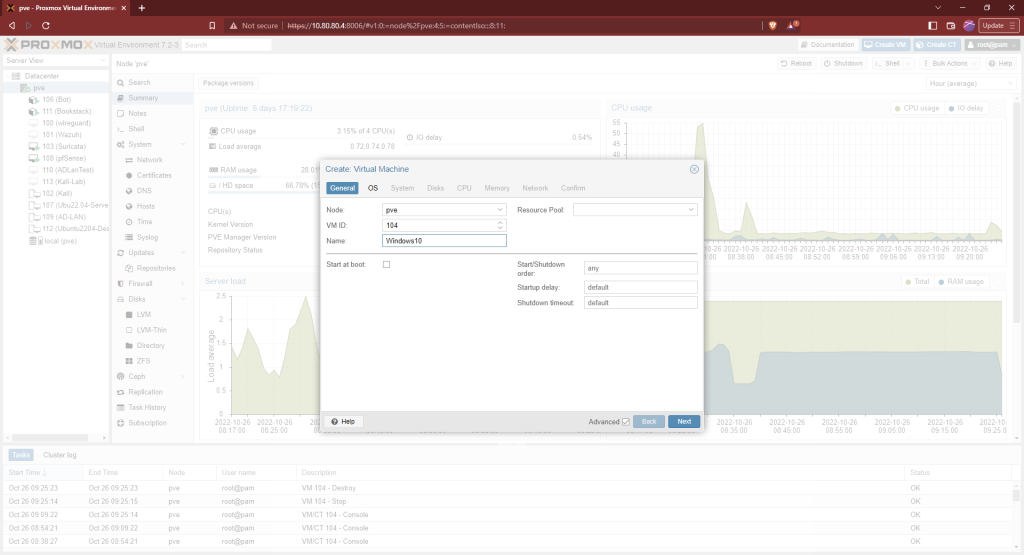
Choose the Windows 10 iso. Select Microsoft Windows as the OS.
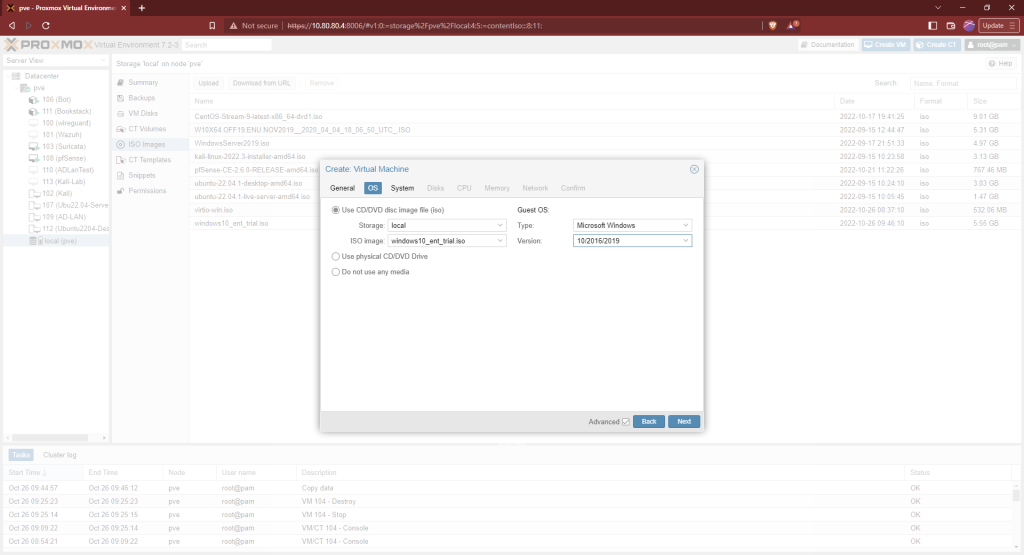
Check the Qemu Agent box. If you don’t see the option, make sure the advanced box is checked on the bottom of the window.
Choose “SCSI” as the bus device. Select “Write Back” for cache and check the “Discard” box.
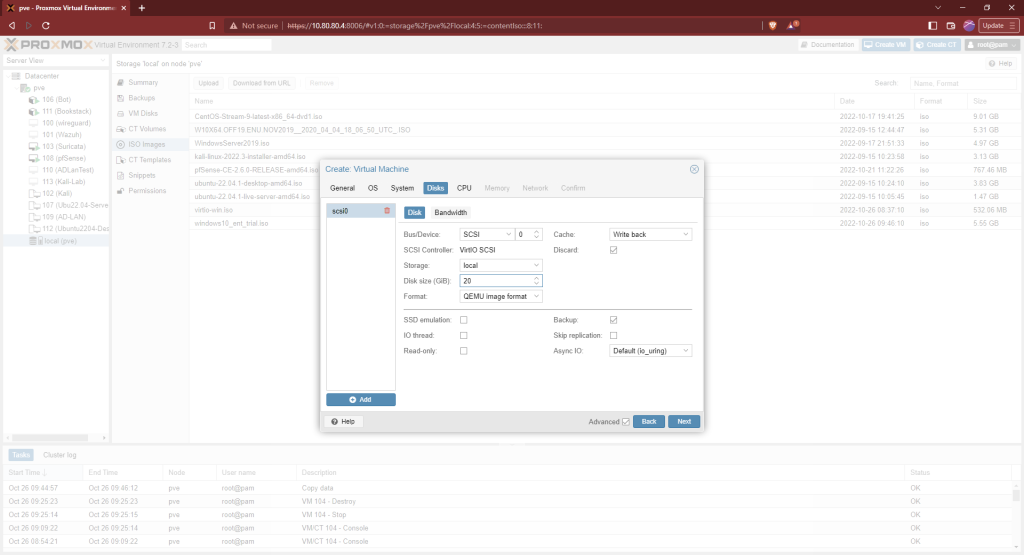
Select the number of cores appropriate for you host system’s resources. I’m using 2 since Proxmox server is being hosted on an older laptop. I’m also going with 2GB of RAM.
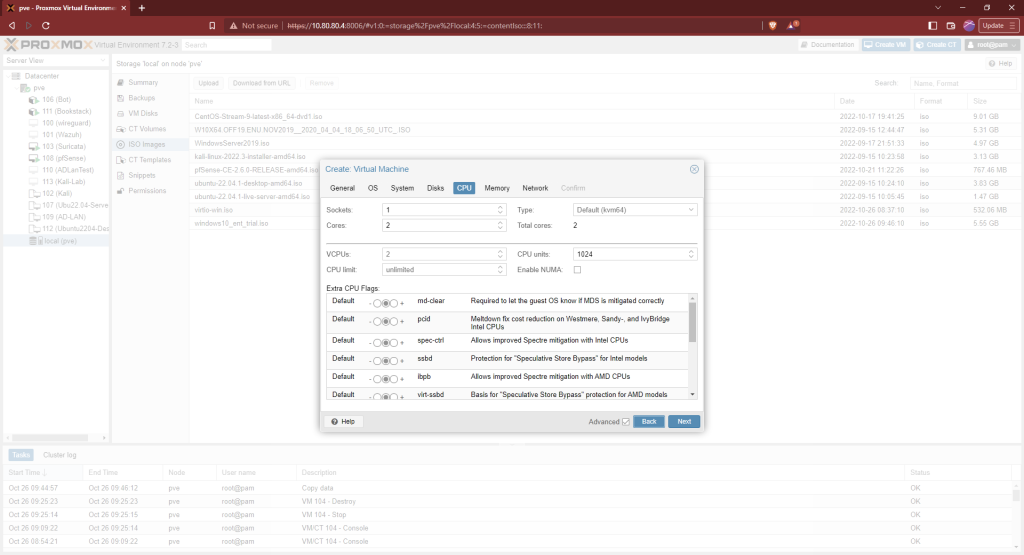
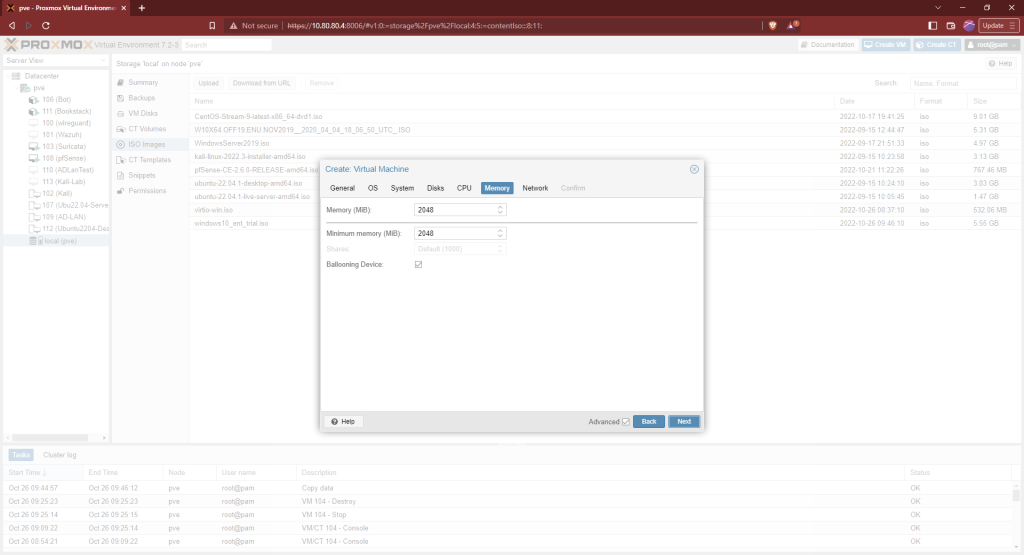
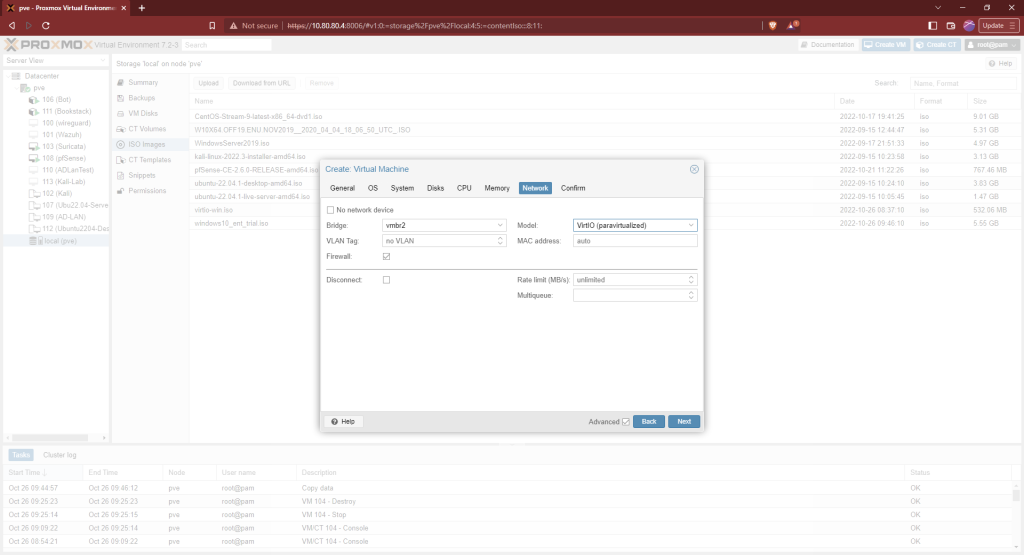
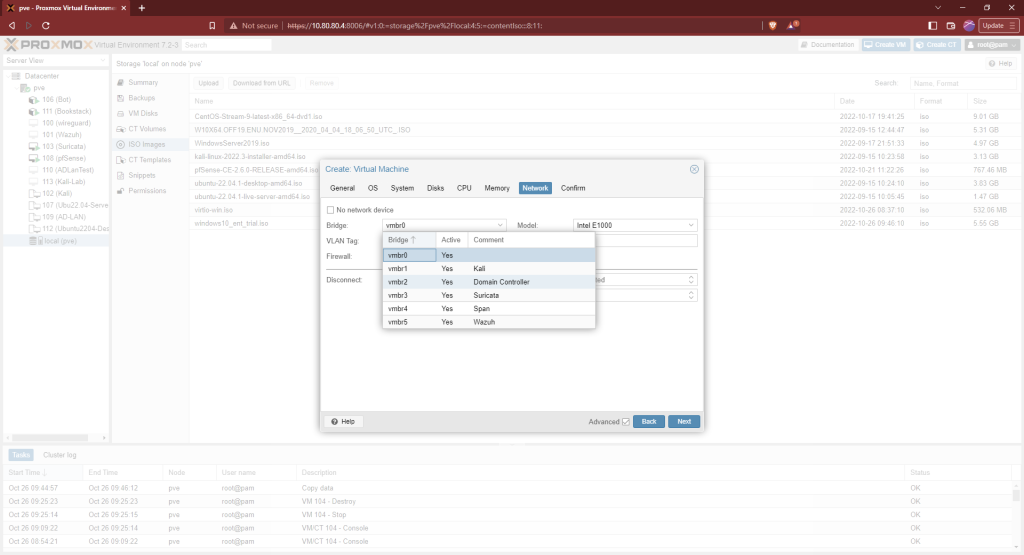
This machine is going on our Active Directory subnet so the network interface will be vmbr2. Change the “Model” to “VirtIO (paravirtualized). Then finish making the VM. Don’t start it yet.
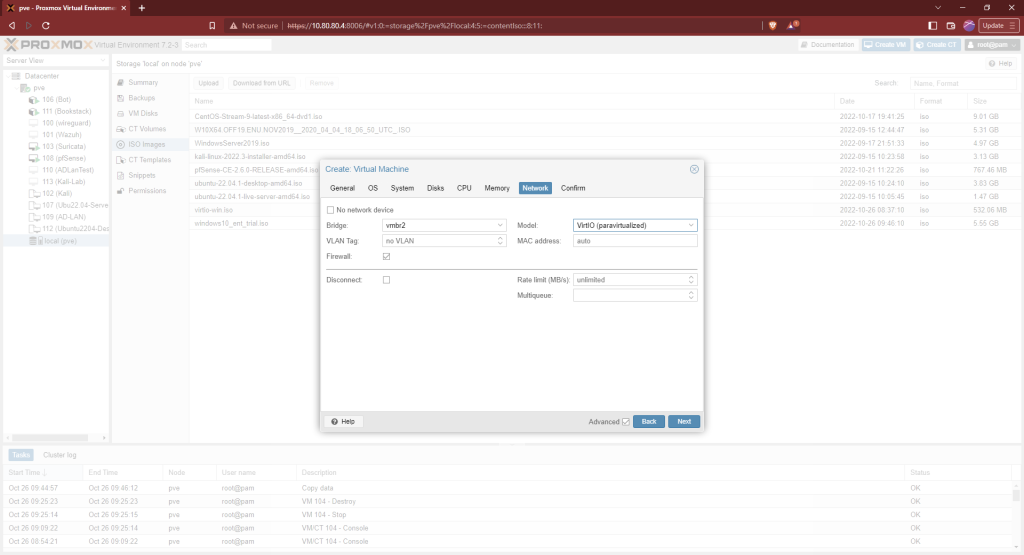
Click on the Windows 10 node that was just made. Click on “Hardware” and then add a new CD/DVD drive.
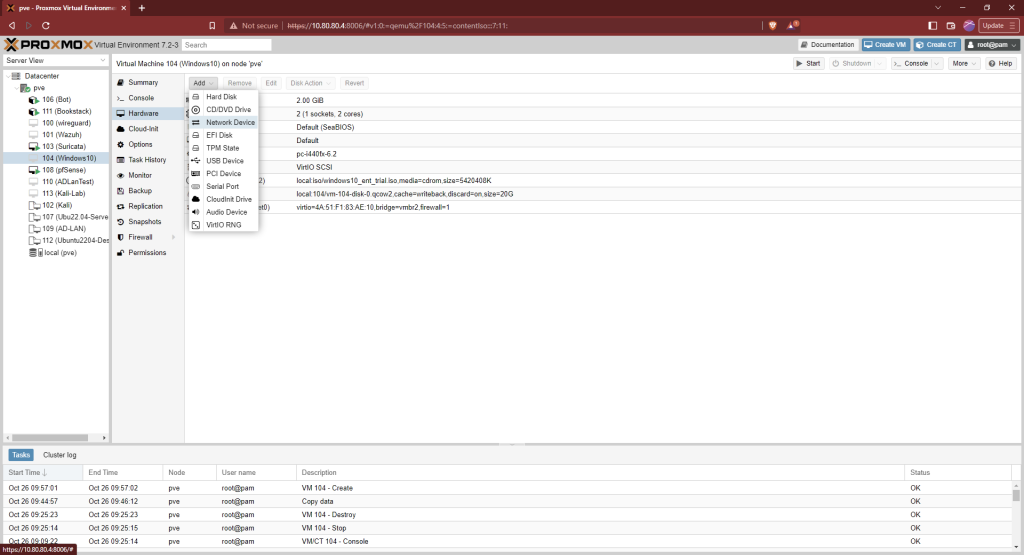
Choose the virtio iso that was downloaded earlier. Now, start the machine.
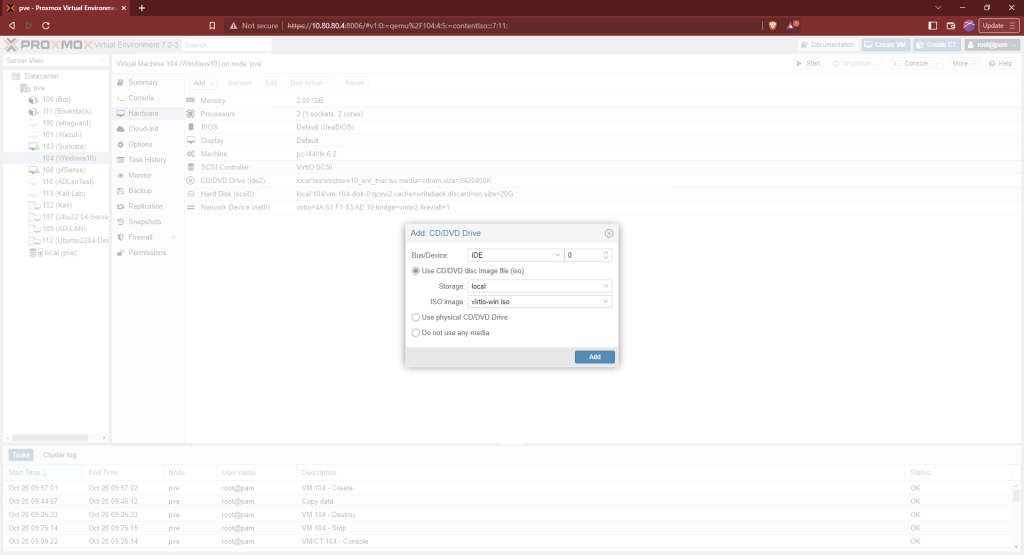
Choose next at the first screen then choose install.
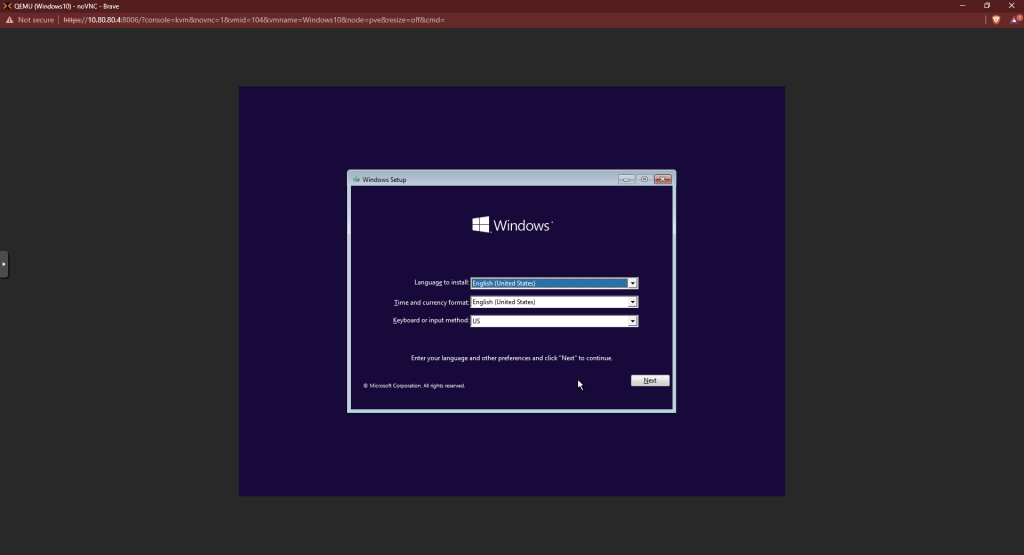
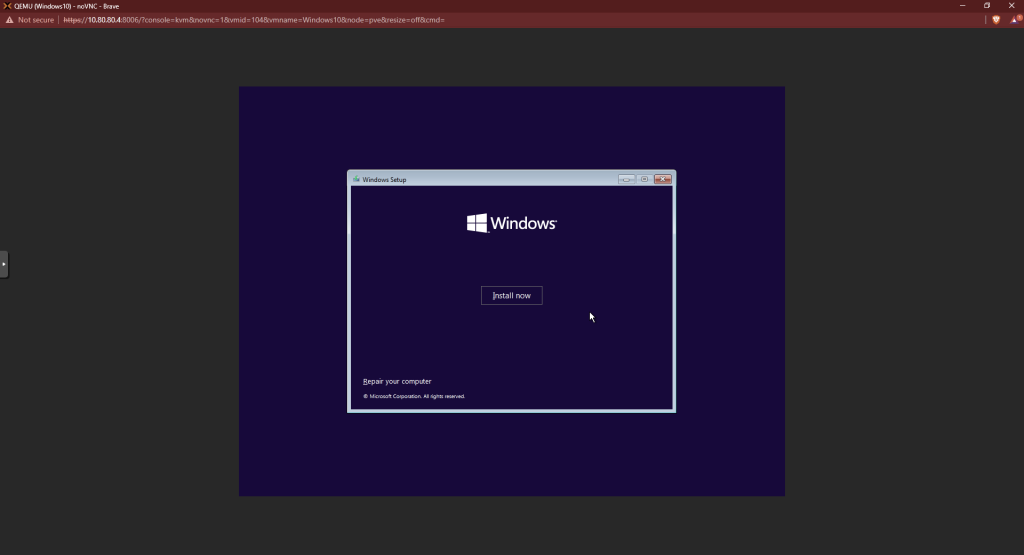
Accept the license terms. Choose custom install.
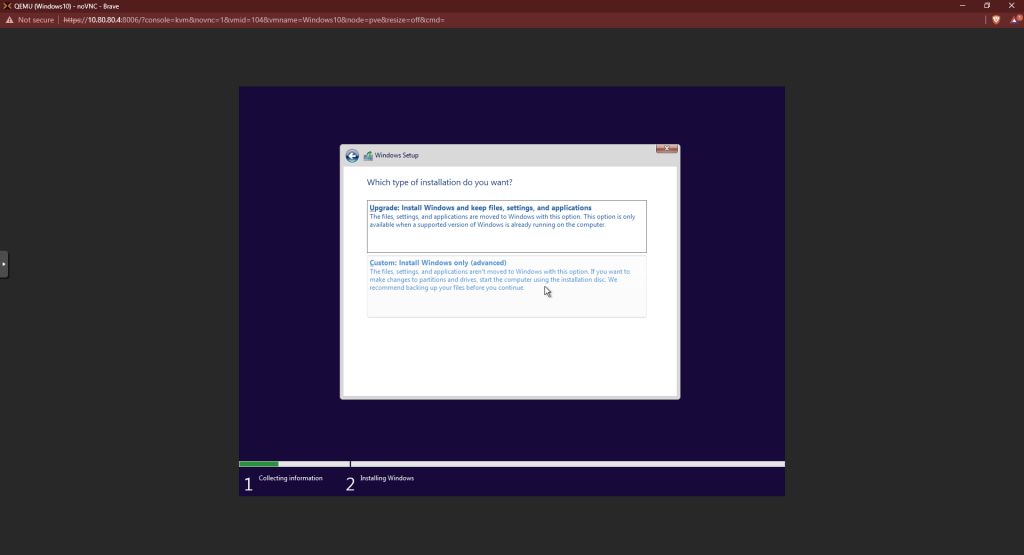
At the next screen, you won’t see a hard drive to choose. That’s normal. Click “Load Driver” from the options at the bottom.
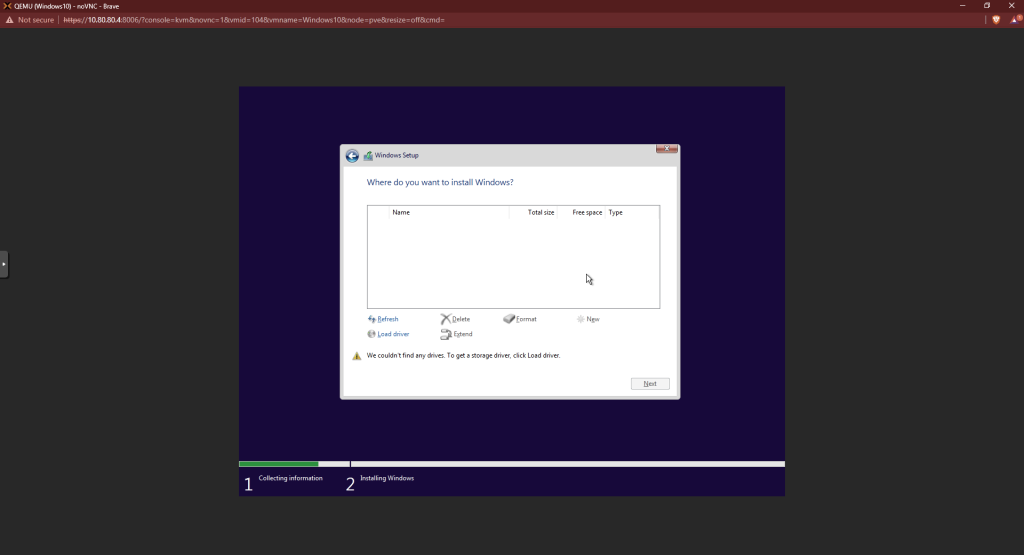
Choose browse at the next screen. Go to the drive with the virtio driver. Go to the vioscsi folder. Under that folder, open the w10 folder and click on the amd64 folder. Then click OK.
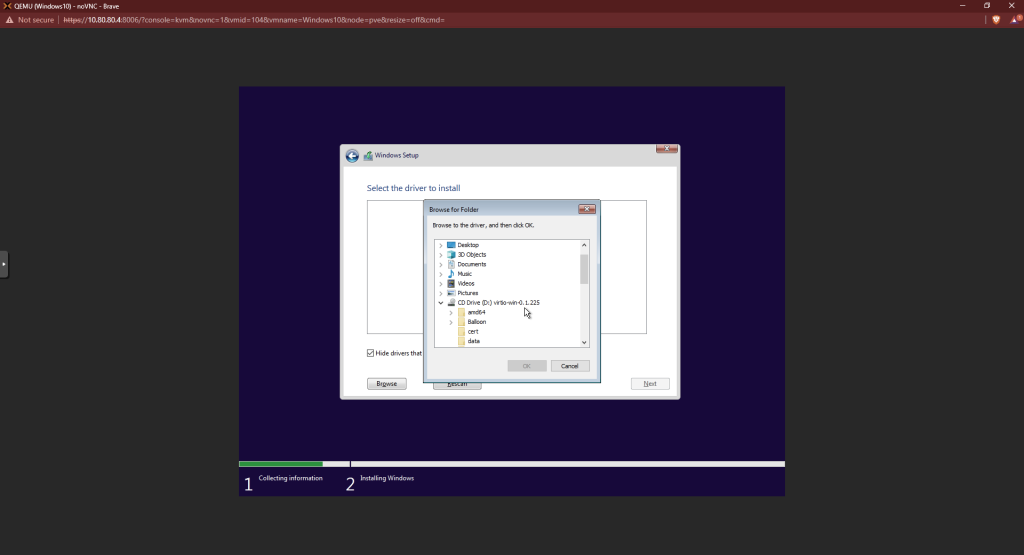
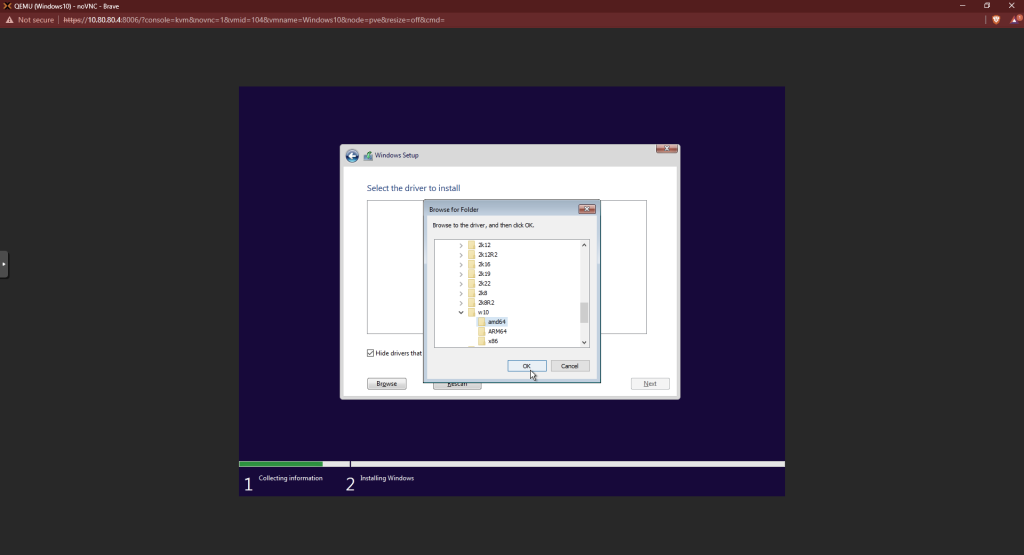
You should see a driver highlighted in the window now. Click next.
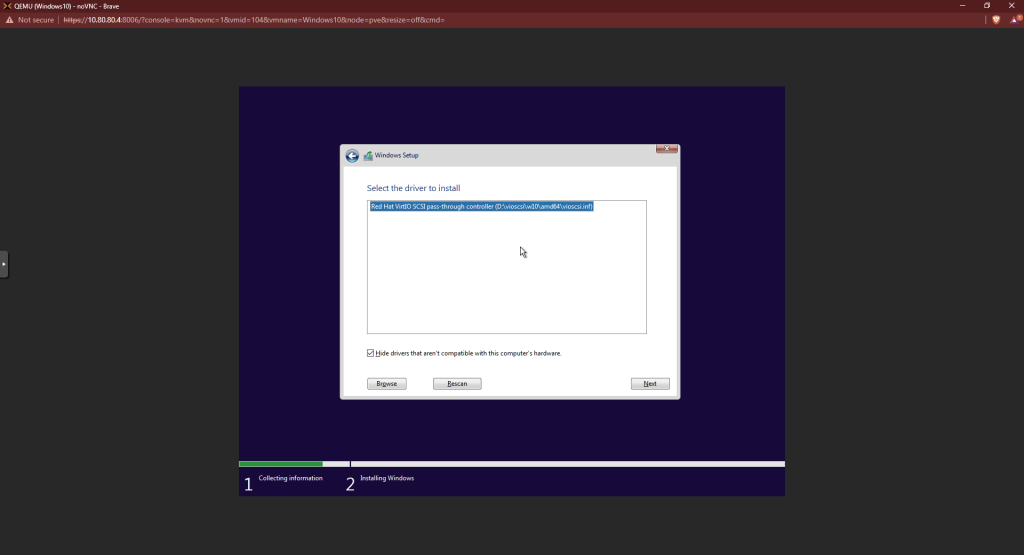
Back at the main screen, you should see there’s a hard drive now. Before continuing, we need to install the network drivers. Click “Load Driver” again.
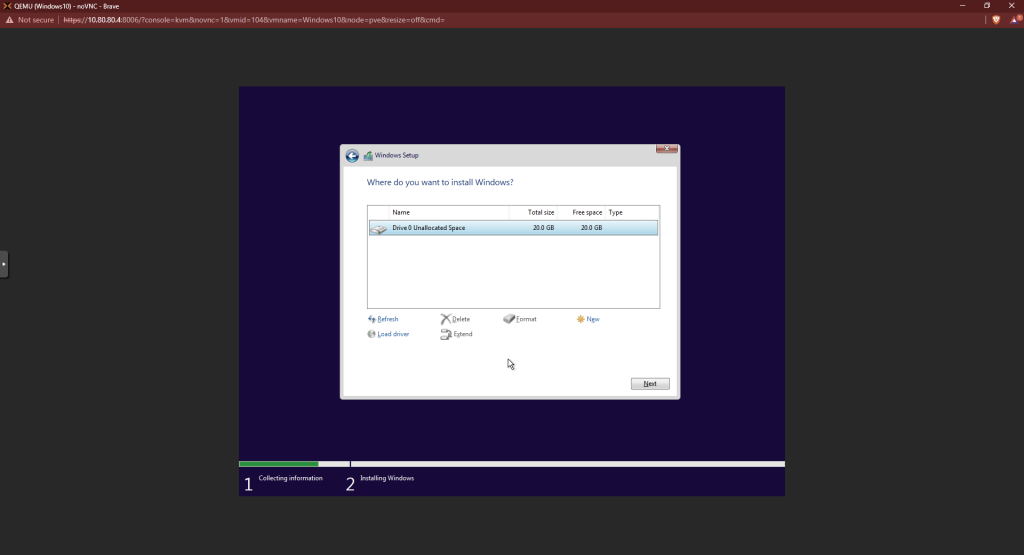
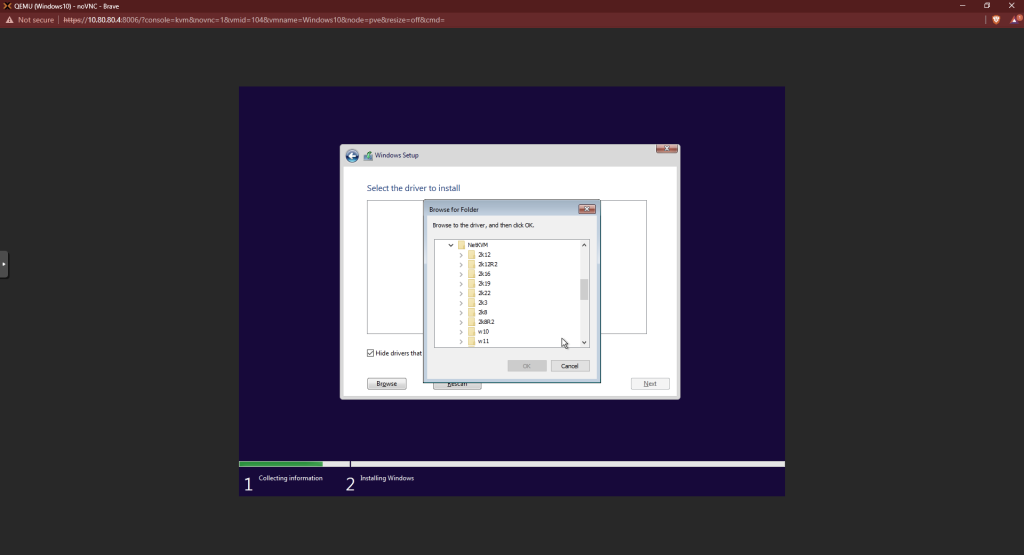
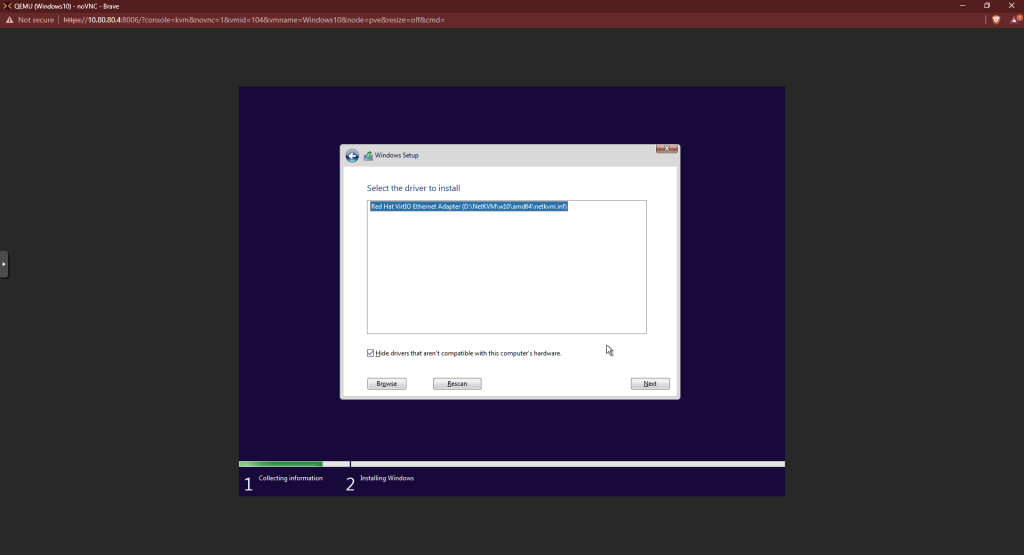
Click next. Wait for the installation to finish.
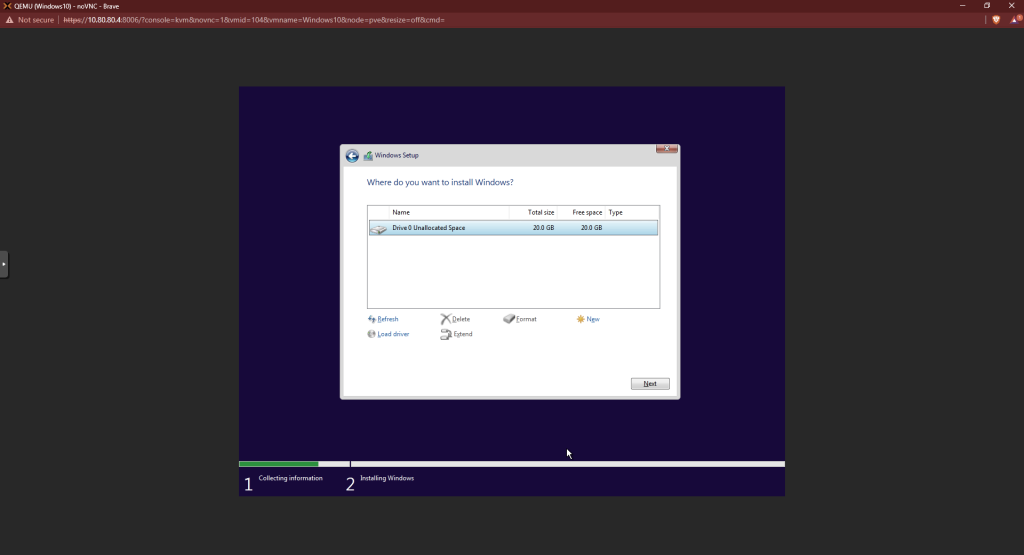
Choose the region and keyboard options appropriate for you.
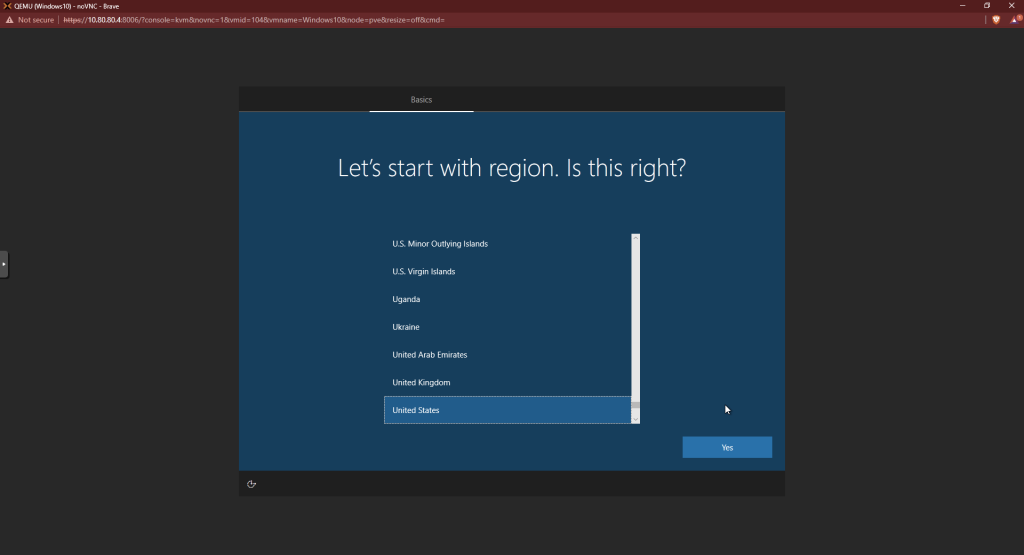
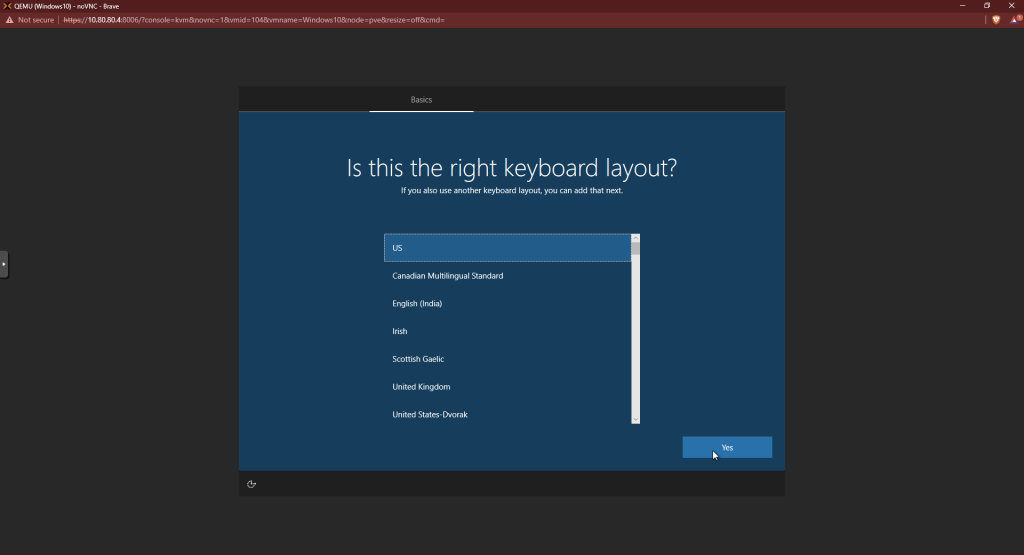
Choose “I don’t have internet.” We’ll configure it later.
Choose “Continue with limited setup.” We’re going to install the least amount of features as possible.
Choose a username for this PC.
Create a password and answers for the security questions.
Turn off all of the extra settings. Decline using Cortana. Wait for the PC to start up.
Join Domain
Open “About PC.” Scroll down to “Rename this PC (Advanced).

Click “Change.”
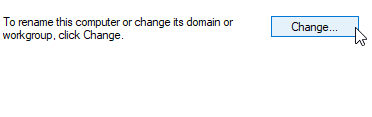
Rename the PC and add the name of the domain.
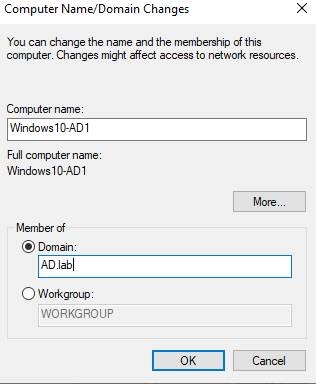
Enter the admin credentials then press “OK.” You should get a confirmation after. Restart the PC.
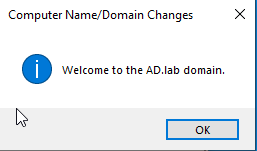
Confirm the computer has joined the domain by checking for it in the Server Manager on the domain controller.
Test Logging in to Domain
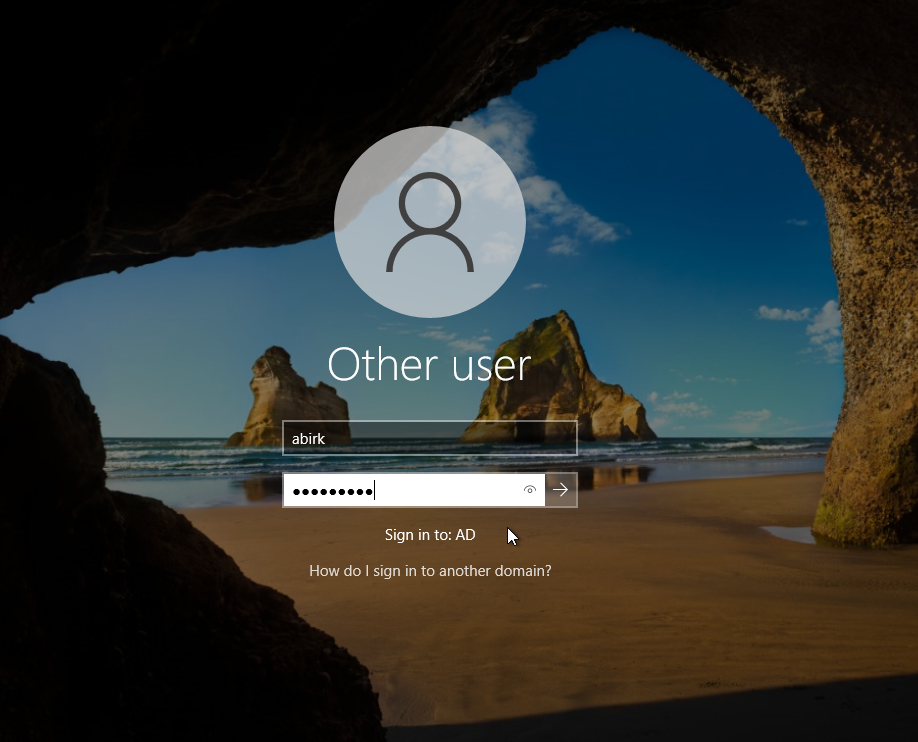
Switch back on the Windows machine. We’re going to log in as one of users created on the domain controller. At the log in screen, choose “Other User.” You should see the name of your domain below the log in fields. Log in with any user and the password will be Password1.
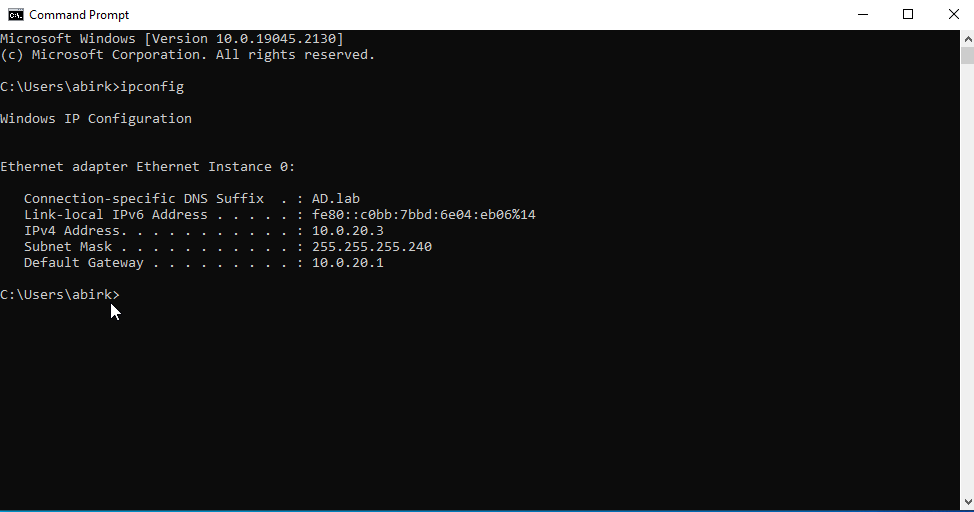
Open the command prompt and run ipconfig. You should see you’re connected to the domain under the “DNS Suffix” line.
Add Group Policy Object
The final thing we’ll do is add a group policy object for restricting the use of removable media. This is a common policy to enforce since removable media can be used both to upload malware to a system or steal information from it.
On Server Manager, go to “Group Policy Management.”
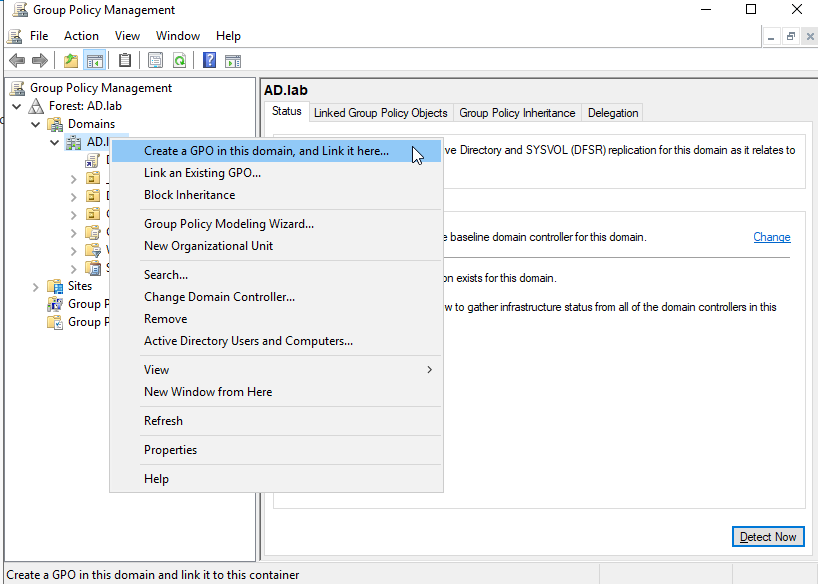
Right-click on the domain node and create and new GPO. This GPO will be for restricting the use of removeable media. Name it “Disable Removable Media.”
Right click on the GPO you just created and click “Edit.” Under “User Configuration,” expand the folder under “Policies”, then “Administrative Templates,” then “System.” Double-click on “Removable Storage Access.”
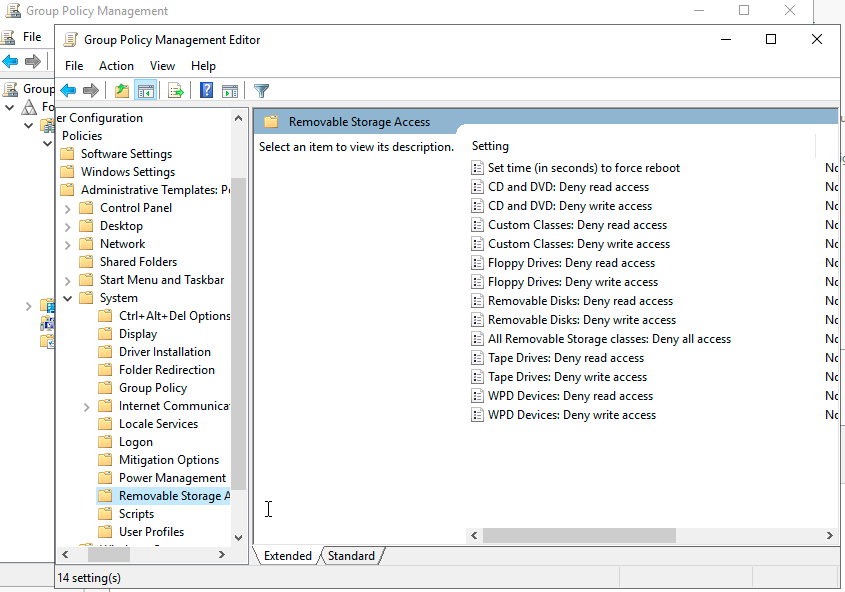
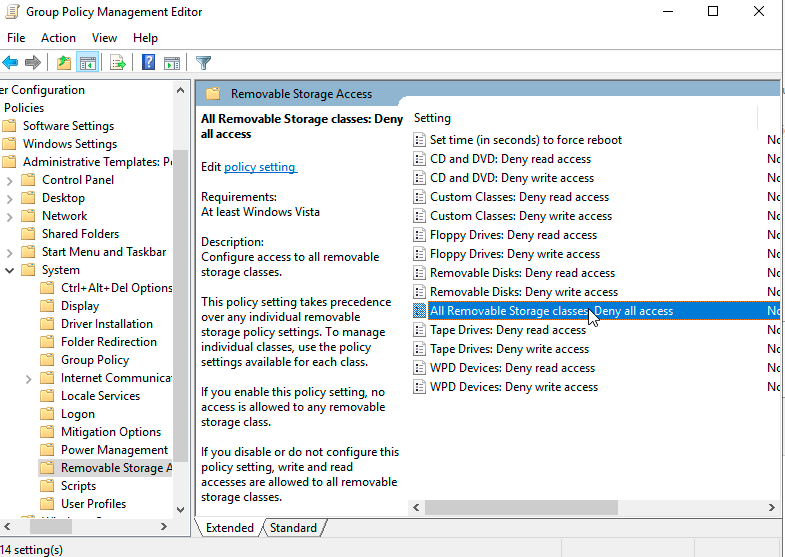
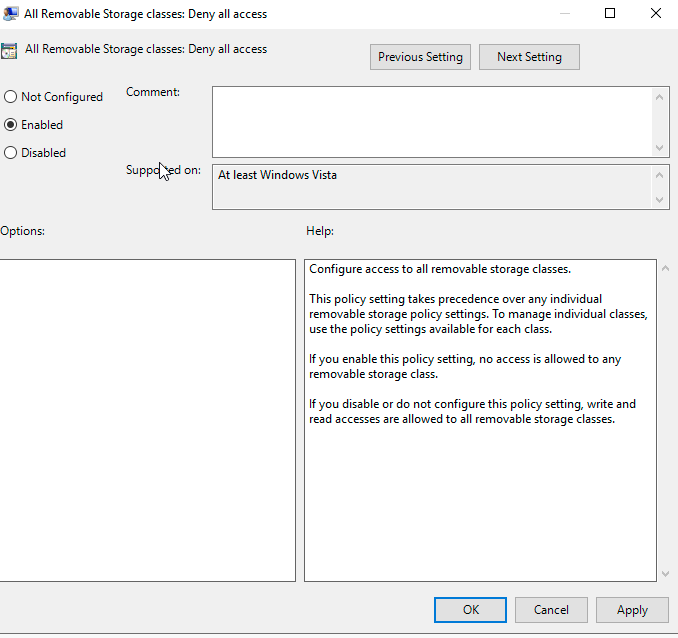
On the window that pops up, click on “Enabled.” Then click “Apply” then “OK.”
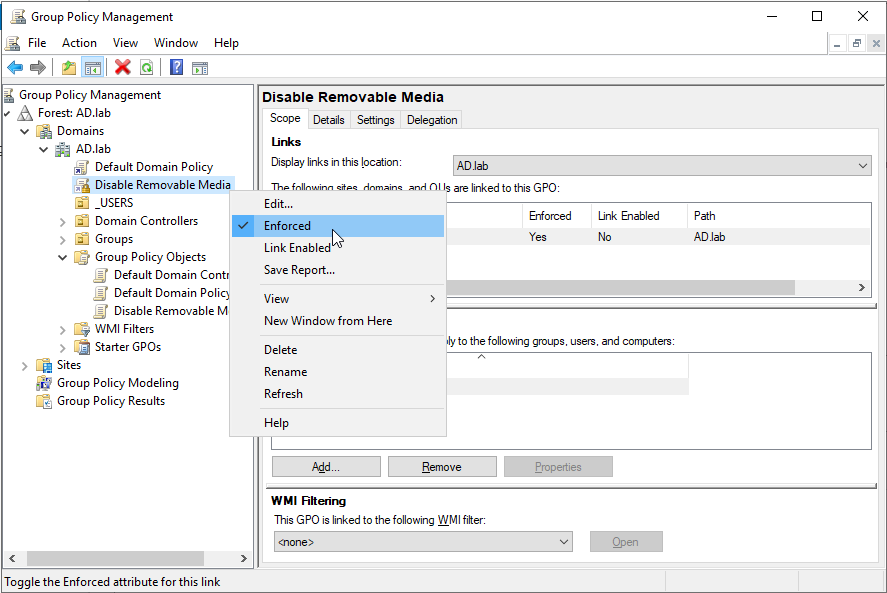
Exit the editor window. Back at the main GPO window, enforce the removable media policy by right-clicking it and clicking “Enforced.”
For the last step, we need to update the new policy for all domain computers. Open powershell as admin and run the command
gpupdate /force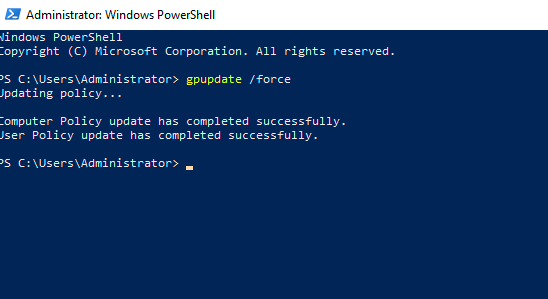
With this update, users cannot read, write, or execute files on removable storage.




